1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
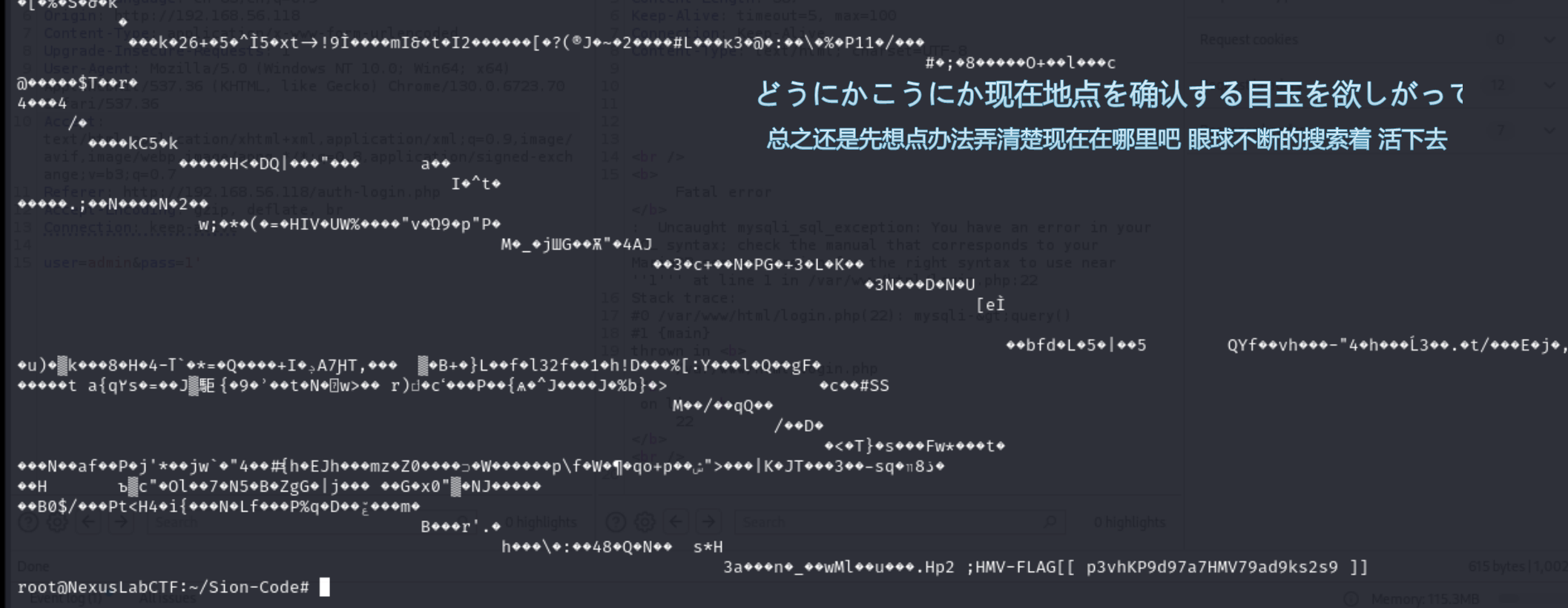
| nmap -T4 -A -v 192.168.56.118
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-06-11 22:47 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 22:47
Completed NSE at 22:47, 0.00s elapsed
Initiating NSE at 22:47
Completed NSE at 22:47, 0.00s elapsed
Initiating NSE at 22:47
Completed NSE at 22:47, 0.00s elapsed
Initiating Ping Scan at 22:47
Scanning 192.168.56.118 [4 ports]
Completed Ping Scan at 22:47, 0.02s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 22:47
Completed Parallel DNS resolution of 1 host. at 22:47, 0.02s elapsed
Initiating SYN Stealth Scan at 22:47
Scanning 192.168.56.118 [1000 ports]
Discovered open port 22/tcp on 192.168.56.118
Discovered open port 80/tcp on 192.168.56.118
Completed SYN Stealth Scan at 22:48, 7.88s elapsed (1000 total ports)
Initiating Service scan at 22:48
Scanning 2 services on 192.168.56.118
Completed Service scan at 22:48, 6.03s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against 192.168.56.118
Retrying OS detection (try #2) against 192.168.56.118
Initiating Traceroute at 22:48
Completed Traceroute at 22:48, 0.02s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 22:48
Completed Parallel DNS resolution of 2 hosts. at 22:48, 0.04s elapsed
NSE: Script scanning 192.168.56.118.
Initiating NSE at 22:48
Completed NSE at 22:48, 5.04s elapsed
Initiating NSE at 22:48
Completed NSE at 22:48, 0.01s elapsed
Initiating NSE at 22:48
Completed NSE at 22:48, 0.00s elapsed
Nmap scan report for 192.168.56.118
Host is up (0.0013s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u5 (protocol 2.0)
| ssh-hostkey:
| 256 48:42:7a:cf:38:19:20:86:ea:fd:50:88:b8:64:36:46 (ECDSA)
|_ 256 9d:3d:85:29:8d:b0:77:d8:52:c2:81:bb:e9:54:d4:21 (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.62 (Debian)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Actiontec MI424WR-GEN3I WAP (99%), DD-WRT v24-sp2 (Linux 2.4.37) (97%), Linux 3.2 (96%), Linux 4.4 (94%), Microsoft Windows XP SP3 or Windows 7 or Windows Server 2012 (92%), VMware Player virtual NAT device (92%), Microsoft Windows XP SP3 (91%), BlueArc Titan 2100 NAS device (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=257 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 1.01 ms 192.168.21.2
2 1.47 ms 192.168.56.118
NSE: Script Post-scanning.
Initiating NSE at 22:48
Completed NSE at 22:48, 0.00s elapsed
Initiating NSE at 22:48
Completed NSE at 22:48, 0.00s elapsed
Initiating NSE at 22:48
Completed NSE at 22:48, 0.00s elapsed
Read data files from: /usr/share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.02 seconds
Raw packets sent: 2072 (94.548KB) | Rcvd: 381 (16.092KB)
|